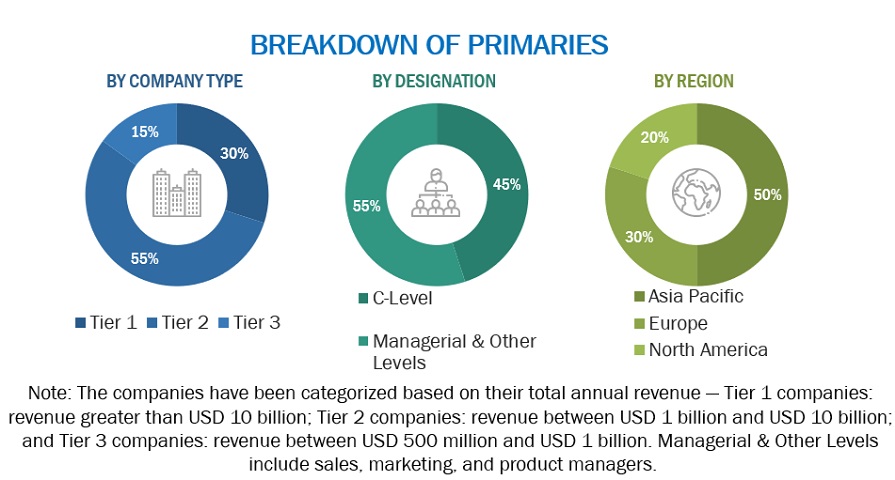
The research study involved significant activities in estimating the identity threat detection and response market size. Exhaustive secondary research utilized various secondary sources about the market and peer markets. To gather information for analyzing the identity threat detection and response market. The next step has been to validate these findings and assumptions and size them with the help of primary research with industry experts across the value chain. Primary sources included interviews with industry experts, suppliers, manufacturers, and other stakeholders across the market's value chain. These interviews with key industry figures and subject matter experts aimed to gather qualitative and quantitative data, ensuring accuracy and reliability in assessing market trends and prospects. Both top-down and bottom-up approaches have been used to estimate the market size. Post which the market breakdown and data triangulation have been adopted to estimate the market sizes of segments and sub-segments.
Secondary Research
In the secondary research process, various secondary sources were referred to identify and collect information for the study. These included journals, annual reports, press releases, investor presentations of companies and white papers, certified publications, and articles from recognized associations and government publishing sources. Secondary research was mainly used to obtain critical information about industry insights, the market's monetary chain, the overall pool of key players, market classification, and segmentation according to industry trends to the bottom-most level, regional markets, and key developments from both market and technology-oriented perspectives.
Primary Research
In the primary research process, various primary sources from both the supply and demand sides were interviewed to obtain qualitative and quantitative information for the report. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Chief Technology Officers (CTOs), Chief Operating Officers (COOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various companies and organizations operating in the identity threat detection and response market. The primary sources from the demand side included consultants/specialists, Chief Information Officers (CIOs), and subject-matter experts.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
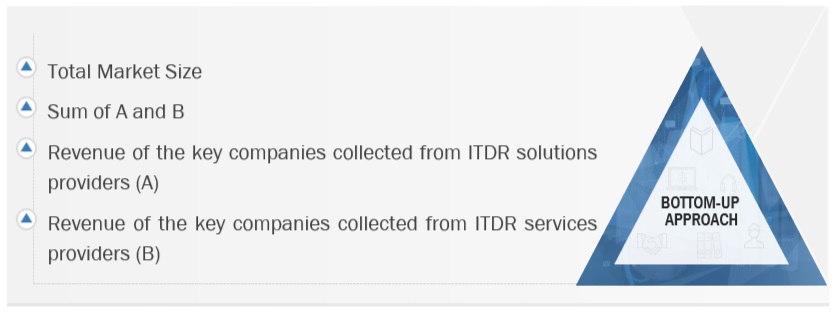
Multiple approaches were adopted to estimate and forecast the identity threat detection and response market. The first approach involved estimating the market size by summating companies' revenue generated through identity threat detection and response solutions.
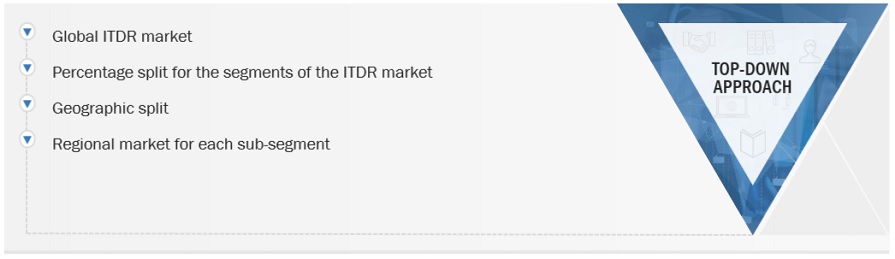
Both top-down and bottom-up approaches were used to estimate and validate the total size of the identity threat detection and response market. The research methodology used to estimate the market size includes the following:
-
Key players in identity threat detection and response were identified through secondary research, and their revenue contributions in the respective regions were determined through primary and secondary research
-
Regarding value, primary and secondary research have determined the industry's supply chain and market size.
-
All percentage shares, splits, and breakups have been determined using secondary sources and verified through primary sources.
All the possible parameters that impact the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. This data is consolidated and added with detailed inputs and analysis from MarketsandMarkets.
Market Size Estimation Methodology-Bottom-up approach
To know about the assumptions considered for the study, Request for Free Sample Report
Market Size Estimation Methodology-top-down approach
Data Triangulation
The data triangulation procedures were used to complete the overall market engineering process and arrive at the exact statistics for all segments and subsegments. The data was triangulated by studying various factors and trends from the demand and supply sides. Along with data triangulation and market breakdown, the market size was validated by the top-down and bottom-up approaches.
Market Definition
Identity threat detection and response (ITDR) is propelled by the continuously evolving global threat landscape and combating threat-targeting identities and identity systems. ITDR provides response strategies ensuring the protection of sensitive and confidential data. It monitors suspicious activities using User Behavior Analytics, Risk-Based Authentication, Managed Detection and Response (MDR), and Threat Intelligence services. Government initiatives promoting digital identity frameworks drive widespread ITDR adoption, fostering innovation and ensuring citizens have secure, portable digital identities.
Key Stakeholders
-
Government bodies and public safety agencies
-
Project managers
-
Developers
-
Business analysts
-
Quality Assurance (QA)/test engineers
-
Consulting firms
-
Third-party vendors
-
Investors and venture capitalists
-
Technology providers
The main objectives of this study are as follows:
-
To describe and forecast the global identity threat detection and response market by offering, deployment mode, organization size, vertical, and region
-
To forecast the market size of five central regions: North America, Europe, Asia Pacific (APAC), Middle East and Africa (MEA), and Latin America
-
To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market
-
To provide detailed information related to significant factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
-
To analyze the opportunities in the market for stakeholders and provide the competitive landscape details of major players
-
To profile the key players of the market and comprehensively analyze their market shares and core competencies
-
To track and analyze competitive developments, such as Mergers and Acquisitions (M&A), new product developments, and partnerships and collaborations in the market
-
To track and analyze the impact of COVID-19 on the identity threat detection and response market
Available Customizations
With the given market data, MarketsandMarkets offers customizations per the company's specific needs. The following customization options are available for the report:
Company Information
-
Detailed analysis and profiling of additional market players (up to 5)



Growth opportunities and latent adjacency in Identity Threat Detection and Response (ITDR) Market