The research study for the AI in Cybersecurity market involved the use of extensive secondary sources and directories, as well as various reputed open-source databases, to identify and collect information useful for this technical and market-oriented study. In-depth interviews were conducted with various primary respondents, including key opinion leaders, subject matter experts, high-level executives of multiple companies providing AI in Cybersecurity offerings, and industry consultants to obtain and verify critical qualitative and quantitative information and assess the market prospects and industry trends.
Secondary Research
In the secondary research process, various sources were referred to for identifying and collecting information for this study. Secondary sources included annual reports, press releases, and investor presentations of companies; white papers, journals, and certified publications; and articles from recognized authors, directories, and databases. The data was also collected from other secondary sources, such as the Data Science Journal, Institute of Electrical and Electronics Engineers (IEEE) Journals and magazines, and other magazines. Secondary research was mainly used to obtain key information about the industry’s value chain and supply chain to identify key players based on hardware, solutions, services, and market classification and segmentation according to offerings of major players, industry trends related to offering, security type, technology, application, verticals, and region, and key developments from both market and technology-oriented perspectives.
Primary Research
In the primary research process, various primary sources from the supply and demand sides of the AI in Cybersecurity market ecosystem were interviewed to obtain qualitative and quantitative information for this study. The primary sources from the supply side included industry experts, such as chief executive officers (CEOs), vice presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various vendors providing AI in Cybersecurity offerings; associated service providers; and system integrators operating in the targeted regions. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data.
After the complete market engineering (including calculations for market statistics, market breakup, market size estimations, market forecast, and data triangulation), extensive primary research was conducted to gather information and verify and validate the critical numbers arrived at. Primary research was also undertaken to identify and validate the segmentation types; industry trends; key players; the market's competitive landscape, and key market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key strategies.
In the complete market engineering process, the top-down and bottom-up approaches and several data triangulation methods were extensively used to perform the market estimation and market forecast for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to record the critical information/insights throughout the report.
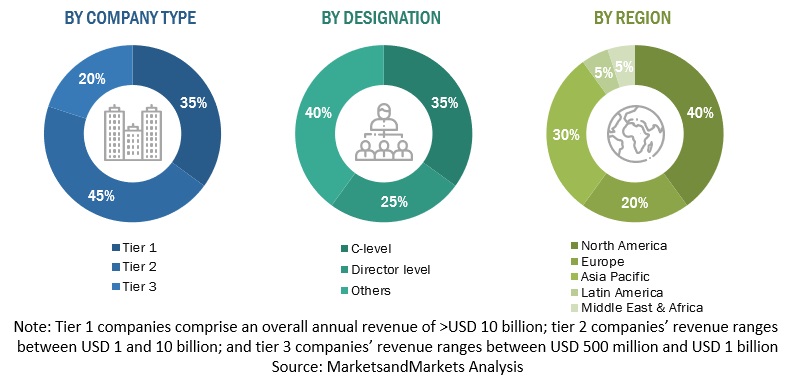
The following is the breakup of primary profiles:
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
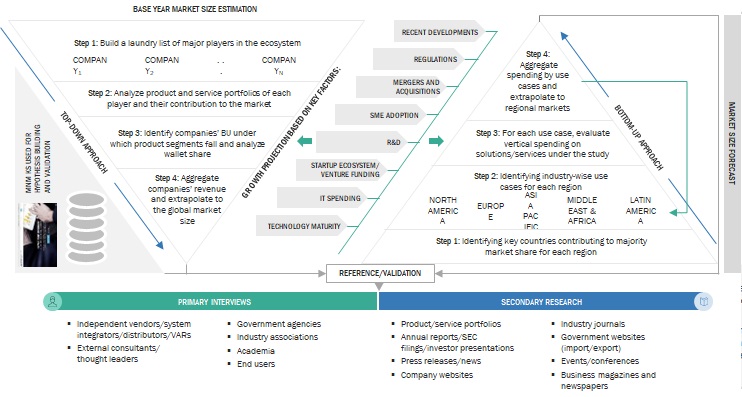
For making market estimates and forecasting the AI in Cybersecurity market and the other dependent submarkets, top-down and bottom-up approaches were used. The bottom-up procedure was used to arrive at the overall market size of the global AI in Cybersecurity market, using the revenue from the key companies and their offerings in the market. With data triangulation and validation through primary interviews, this study determined and confirmed the exact value of the overall parent market size. The overall market size was then used in the top-down procedure to estimate the size of other individual markets via percentage splits of the market segments.
The top-down approach prepared an exhaustive list of all the vendors offering AI in Cybersecurity. The revenue contribution of the market vendors was estimated through annual reports, press releases, funding, investor presentations, paid databases, and primary interviews. Each vendor’s offerings were evaluated based on the breadth of solution and service offerings, cloud types, organization sizes, and verticals. The aggregate of all the companies' revenues was extrapolated to reach the overall market size. Each subsegment was studied and analyzed for its global market size and regional penetration. The markets were triangulated through both primary and secondary research. The primary procedure included extensive interviews for key insights from industry leaders, such as CIOs, CEOs, VPs, directors, and marketing executives. The market numbers were further triangulated with the existing MarketsandMarkets repository for validation.
In the bottom-up approach, the adoption rate of AI in Cybersecurity hardware, solutions, and services among different end-users in key countries with respect to their regions contributing the most to the market share was identified. For cross-validation, the adoption of AI in Cybersecurity hardware, solutions, and services among industries, along with different use cases with respect to their regions, was identified and extrapolated. Weightage was given to use cases identified in different regions for the market size calculation.
All the possible parameters that affect the market covered in the research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. The data is consolidated and added with detailed inputs and analysis from MarketsandMarkets.
-
The pricing trend is assumed to vary over time.
-
All the forecasts are made with the standard assumption that the accepted currency is USD.
-
For the conversion of various currencies to USD, average historical exchange rates are used according to the year specified. For all the historical and current exchange rates required for calculations and currency conversions, the US Internal Revenue Service’s website is used.
-
All the forecasts are made under the standard assumption that the globally accepted currency, USD, remains constant during the next five years.
-
Vendor-side analysis: The market size estimates of associated solutions and services are factored in from the vendor side by assuming an average of licensing and subscription-based models of leading and innovative vendors.
-
Demand/end-user analysis: End users operating in verticals across regions are analyzed in terms of market spending on AI in Cybersecurity solutions and services based on some of the key use cases. These factors for the AI in Cybersecurity tool industry per region are separately analyzed, and the average spending was extrapolated with an approximation based on assumed weightage. This factor is derived by averaging various market influencers, including recent developments, regulations, mergers and acquisitions, enterprise/SME adoption, startup ecosystem, IT spending, technology propensity and maturity, use cases, and the estimated number of organizations per region.
Market Size Estimation: Top Down And Bottom Up Approach
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
After arriving at the overall market size using the market size estimation processes as explained above, the market was split into several segments and subsegments. To complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment, data triangulation and market breakup procedures were employed, wherever applicable. The overall market size was then used in the top-down procedure to estimate the size of other individual markets via percentage splits of the market segmentation.
Market Definition
Cybersecurity is a set of processes and practices designed to safeguard endpoints, networks, applications, and data from advanced threats and vulnerabilities. Enterprises are required to adopt a set of security technologies, solutions, tools, policies, security concepts, guidelines, risk management approaches, and services to protect critical enterprise information and infrastructure from the growing volume and sophistication of cyberattacks. In such situations, AI in security is used to predict outcomes based on past events. AI software identifies patterns and anomalies pertaining to past events, thereby identifying threats across a firm's network, both on-premises and in the cloud, to mitigate further attacks.
Key Stakeholders
-
AI Solution Providers
-
AI Platform Providers
-
Cloud Service Providers
-
AI System Providers
-
Universities and Research Organizations
-
Investors and Venture Capitalists
-
Managed service providers
-
Support and maintenance service providers
-
System Integrators (SIs)/migration service providers
-
Value-Added Resellers (VARs) and distributors
-
Distributors and Value-added Resellers (VARs)
-
System Integrators (SIs)
-
Independent Software Vendors (ISV)
-
Third-party providers
-
Technology providers
-
Semiconductor Companies
Report Objectives
-
To describe and forecast the artificial intelligence in cybersecurity market, in terms of value,
by offering, security type, technology, application, and vertical
-
To describe and forecast the artificial intelligence in cybersecurity market, in terms of value,
by region—North America, Europe, Asia Pacific, Middle East & Africa and Latin America
-
To provide detailed information regarding major factors influencing the market growth (drivers, restraints, opportunities, and challenges)
-
To strategically analyze micromarkets1 with respect to individual growth trends, prospects, and contribution to the overall artificial intelligence in cybersecurity market
-
To profile key players and comprehensively analyze their market positions in terms of ranking and core competencies2, along with detailing the competitive landscape for market leaders
-
To analyze competitive developments such as joint ventures, mergers and acquisitions, product developments, and ongoing research and development (R&D) in the artificial intelligence in cybersecurity market
-
To provide the illustrative segmentation, analysis, and projection of the main regional markets
Available Customizations
With the given market data, MarketsandMarkets offers customizations as per the company’s specific needs. The following customization options are available for the report:
Product Analysis
-
Product matrix provides a detailed comparison of the product portfolio of each company
Geographic Analysis
-
Further breakup of the North American market for AI in Cybersecurity
-
Further breakup of the European market for AI in Cybersecurity
-
Further breakup of the Asia Pacific market for AI in Cybersecurity
-
Further breakup of the Latin American market for AI in Cybersecurity
-
Further breakup of the Middle East & Africa market for AI in Cybersecurity
Company Information
-
Detailed analysis and profiling of additional market players (up to five)



Growth opportunities and latent adjacency in Artificial Intelligence in Cybersecurity Market