The market size of zero trust security was ascertained through a range of essential research efforts. A lot of secondary research was done to learn more about the sector. Primary research with industry professionals from all points of the value chain then confirmed these conclusions, hypotheses, and estimates. A variety of strategies, including top-down and bottom-up approaches, were used to estimate the total market size. The market sizes of the various segments and subsegments within the zero trust security market were then determined using market segmentation and data triangulation approaches.
Secondary Research
During the secondary research phase, various sources were looked into to gather information for the study. These secondary sources included annual reports, press releases, investor presentations from Zero Trust Security software and service providers, online forums, accredited publications and white papers. This secondary research was used to get insights into the industry supply chain, key players, market segmentation down to granular level, regional markets and notable developments from market and technology perspective. These findings were then validated through primary sources. Factors considered to estimate regional market size included government and technology initiatives, Gross Domestic Product (GDP) growth rates, Information and Communication Technology (ICT) spend, recent market developments and a thorough analysis of major Operational Technology Security solution providers’ market position.
Primary Research
The comprehensive market engineering process employed a combination of top-down and bottom-up approaches, complemented by various data triangulation methods, to estimate accurately and forecast market trends for overall market segments and subsegments outlined in the report. The report accordingly compiled and presented key insights and information through accurate qualitative and quantitative analyses ran throughout the market engineering process.
After completing the market engineering process, which encloses calculations for market statistics, segmentation breakdowns, market size estimations, forecasts, and data triangulation, thorough primary research was conducted. This primary research gathered, verified, and validated critical numerical data and identified segmentation types, industry trends, and the competitive landscape within the Zero Trust Security market. The primary research was instrumental in elucidating fundamental market dynamics, Including drivers, restraints, opportunities, challenges, industry trends, and strategic initiatives market players adopt.
Following is the breakup of the primary study:
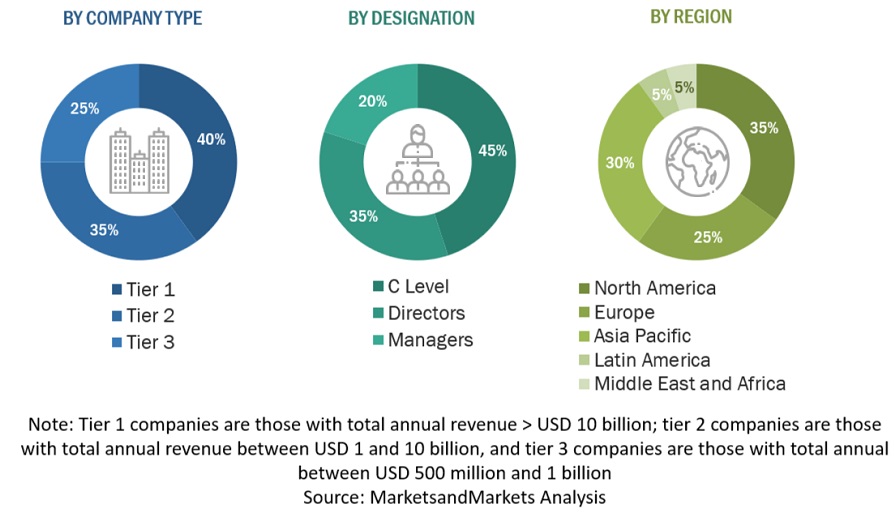
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Both top-down and bottom-up methods were implemented to get an accurate picture of the global Zero Trust Security market's size. Also evaluated the sizes of different parts within this bigger market. This approach had several steps:First, Identifying the main players in the market through a lot of background reading. Then, looked at the revenue made in different Regions by the players. To do this, Have gone through reports and spoken to people in charge. Spent time looking at yearly and revenue reports from the top companies. Also had primary interviews with industry leaders like CEOs, VPs, directors, and marketing bosses to learn more. All the numbers about market splits and different parts came from reading reports. Re-ensured these numbers were Accurate by talking to Officials.
INFOGRAPHIC DEPICTING BOTTOM-UP AND TOP-DOWN APPROACHES
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
Following the determination of the overall market size using the market above size estimation methodologies, the market was segmented into distinct segments and subsegments. Data triangulation and market segmentation procedures were utilized, as needed, to complete the comprehensive market engineering process and ascertain the precise statistics for each market segment and subsegment. Data triangulation was achieved by analyzing various factors and trends from both the demand and supply sides.
Market Definition
The US National Institute of Standards and Technology (NIST), in its current draft of standards for zero trust architecture, defines zero trust in the following manner: “Zero trust is a cybersecurity paradigm focused on resource protection and the premise that trust is never granted implicitly but must be continually evaluated.” Zero trust security is, therefore, not only a product or an approach—it is a web of connected policies, practices, software, and hardware that create an entire zero-trust ecosystem.
According to CrowdStrike, zero trust is a security concept that requires all users, even those inside the organization’s enterprise network, to be authenticated, authorized, and continuously validating security configuration and posture before being granted or keeping access to applications and data.
Further, according to Akamai Technologies, zero trust is a network security model, based on a strict identity verification process. The framework dictates that only authenticated and authorized users and devices can access applications and data. At the same time, it protects those applications and users from advanced threats on the Internet”.
Report Objectives
-
To define, describe, and forecast the Zero Trust Security market based on offering, application, security type, authentication type, vertical, and region.
-
To forecast the market size of five central regions: North America, Europe, Asia Pacific (APAC), Middle East & Africa (MEA), and Latin America.
-
To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market.
-
To provide detailed information related to the primary factors (drivers, restraints, opportunities, and challenges) influencing the growth of Zero Trust Security market.
-
To analyze opportunities in the market for stakeholders by identifying high-growth segments of the Zero Trust Security market.
-
To profile the key players of the Zero Trust Security market and comprehensively analyze their market size and core competencies.
-
Track and analyze competitive developments, such as new product launches, mergers and acquisitions, partnerships, agreements, and collaborations in the global Zero Trust Security market.
Customization Options
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis
-
Further breakup of the Asia Pacific market into major countries.
-
Further breakup of the North American market into major countries.
-
Further breakup of the Latin American market into major countries.
-
Further breakup of the Middle East African market into major countries
-
Further breakup of the European market into major countries.
Company Information
-
Detailed analysis and profiling of additional market players (up to 5)



Growth opportunities and latent adjacency in Zero Trust Security Market