The research encompassed various vital activities to determine the current market size of the threat-hunting market. Extensive secondary research was conducted to gather information on the industry. Subsequently, primary research involving industry experts across the value chain validated these findings, assumptions, and estimations. The total market size was estimated using different methodologies, including top-down and bottom-up approaches. Following this, market segmentation and data triangulation techniques were applied to ascertain the market size of individual segments and subsegments within the Threat hunting market.
Secondary Research
During the secondary research phase, various sources were consulted to identify and gather pertinent information for the study. These secondary sources encompassed annual reports, press releases, investor presentations from Threat hunting software and service vendors, online forums, accredited publications, and white papers. This secondary research served as a foundation for acquiring crucial insights into the industry's supply chain, key players, market categorization, segmentation based on prevailing trends down to granular levels, regional markets, and noteworthy developments from both market and technological perspectives. These findings were subsequently corroborated and validated through primary sources. Factors considered in estimating regional market sizes included governmental and technological initiatives, Gross Domestic Product (GDP) growth rates, Information and Communication Technology (ICT) expenditure, recent market developments, and a comprehensive analysis of significant Operational Technology Security solution providers' market standings.
Primary Research
The comprehensive market engineering process employed a combination of top-down and bottom-up approaches, complemented by various data triangulation methods, to accurately estimate and forecast market trends for overall market segments and subsegments outlined in the report. The report systematically compiled and presented vital insights and information through meticulous qualitative and quantitative analyses conducted throughout the market engineering process.
After completing the market engineering process, which encompassed calculations for market statistics, segmentation breakdowns, market size estimations, forecasts, and data triangulation, thorough primary research was undertaken. This primary research gathered, verified, and validated critical numerical data and identified segmentation types, industry trends, and the competitive landscape within the Threat hunting market. Moreover, primary research was instrumental in elucidating fundamental market dynamics, including drivers, restraints, opportunities, challenges, industry trends, and strategic initiatives market players adopt.
Following is the breakup of the primary study:
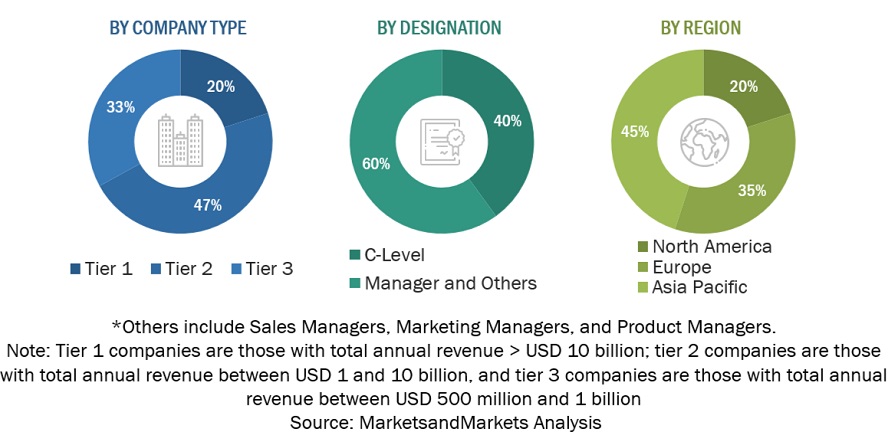
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Both top-down and bottom-up approaches were employed to accurately estimate and validate the size of the global Threat hunting market and determine the sizes of various dependent subsegments within the overarching Threat hunting market. The research methodology utilized for estimating market size involved several key steps: Initially, the identification of key players in the market was conducted through comprehensive secondary research. Subsequently, their revenue contributions within respective regions were assessed through a combination of primary and secondary research methods. This process entailed thoroughly examining leading market players' annual and financial reports, supplemented by extensive interviews with industry leaders, including CEOs, VPs, directors, and marketing executives, to gain valuable insights. All percentage splits and segment breakdowns were derived from secondary sources and cross-validated through primary sources to ensure accuracy and reliability.
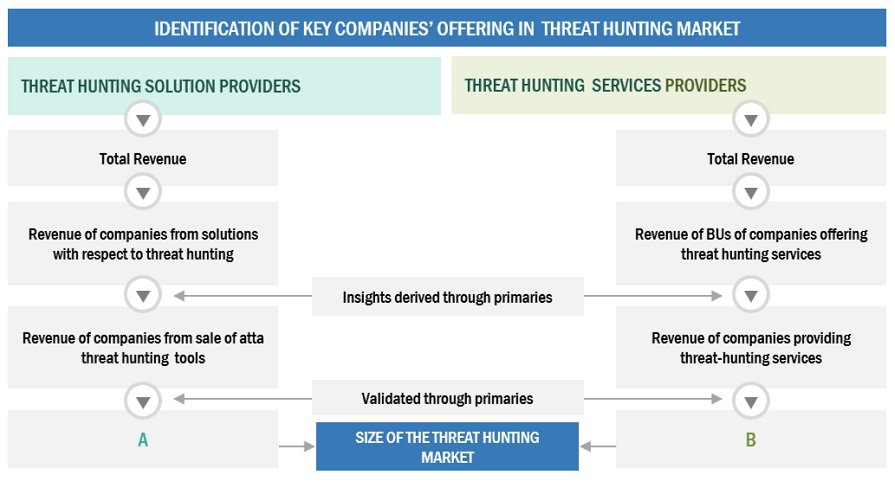
To know about the assumptions considered for the study, Request for Free Sample Report
Infographic Depicting Bottom-Up And Top-Down Approaches
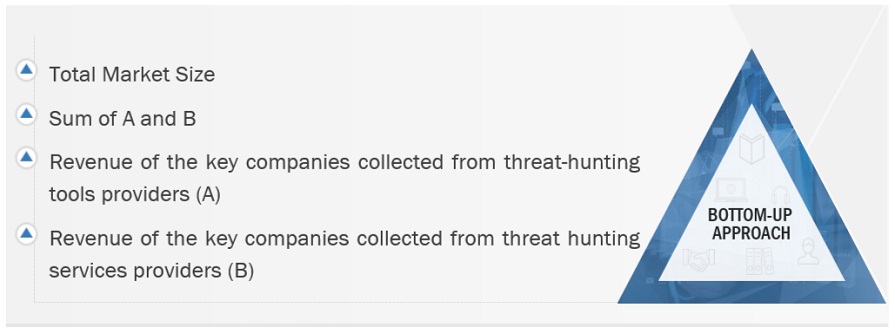
Market Size Estimation Methodology-top-down approach
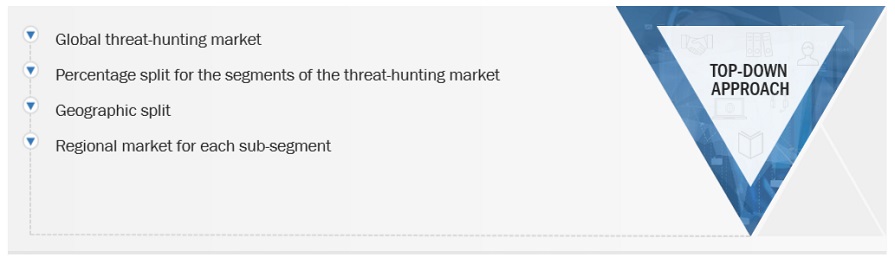
Data Triangulation
Following the determination of the overall market size using the market above size estimation methodologies, the market was segmented into distinct segments and subsegments. Data triangulation and market segmentation procedures were utilized, as needed, to complete the comprehensive market engineering process and ascertain the precise statistics for each market segment and subsegment. Data triangulation was achieved by analyzing various factors and trends from both the demand and supply sides.
Market Definition
As per IBM, Threat hunting, also known as cyber threat hunting, is a proactive approach to identifying previously unknown or ongoing non-remediated threats within an organization's network.
Cyber or proactive threat hunting seeks out unknown cybersecurity threats to a network. Threat hunting involves searching through endpoints, networks, systems, applications, sources, and datasets to hunt or identify malicious or suspicious activity.
Key Stakeholders
-
Chief technology and data officers
-
Certified information system auditors
-
Business analysts
-
Information technology (IT) professionals
-
Government agencies
-
Small and medium-sized enterprises (SMEs) and large enterprises
-
Consultants/consultancies/advisory firms
-
Managed and professional service providers
Report Objectives
-
To define, describe, and forecast the Threat hunting market based on offering, threat type, organization size, deployment mode, vertical, and region.
-
To forecast the market size of five central regions: North America, Europe, Asia Pacific (APAC), Middle East & Africa (MEA), and Latin America.
-
To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market.
-
To provide detailed information related to the primary factors (drivers, restraints, opportunities, and challenges) influencing the growth of market.
-
To analyze opportunities in the market for stakeholders by identifying high-growth segments of the market.
-
To profile the key players of the market and comprehensively analyze their market size and core competencies.
-
Track and analyze competitive developments, such as new product launches, mergers and acquisitions, partnerships, agreements, and collaborations in the global Threat hunting market.
Customization Options
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis
-
Further breakup of the Asia Pacific market into major countries.
-
Further breakup of the North American market into major countries.
-
Further breakup of the Latin American market into major countries.
-
Further breakup of the Middle East African market into major countries
-
Further breakup of the European market into major countries.
Company Information
-
Detailed analysis and profiling of additional market players (up to 5)



Growth opportunities and latent adjacency in Threat Hunting Market