This research study involved the extensive use of secondary sources, directories, and databases, such as the Stockholm International Peace Research Institute (SIPRI), Department of Defense (DoD), UN Comtrade, Organization for Economic Cooperation and Development (OECD), and Factiva, to identify and collect relevant information on the defense cybersecurity market. Primary sources included industry experts from the concerned market, preferred suppliers, manufacturers, solution providers, technology developers, alliances, and organizations related to all segments of the value chain. All primary sources were interviewed to obtain and verify critical qualitative and quantitative information as well as assess the prospects of the market.
In-depth interviews were conducted with various primary respondents, including key industry participants, subject-matter experts, C-level executives of key market players, and industry consultants, among others, to obtain and verify critical qualitative and quantitative information and to assess future prospects of the market.
Secondary Research
The market share of companies in the defense cybersecurity market was determined using secondary data made available through paid and unpaid sources and by analyzing product portfolios of major companies operating in the market. These companies were rated based on the performance and quality of their products. These data points were further validated by primary sources.
Secondary sources that were referred to for this research study on the defense cybersecurity market included government sources such as the US Department of Defense (DoD), defense budgets, military modernization program documents, corporate filings such as annual reports, investor presentations, and financial statements, and trade, business, and professional associations. This secondary data was collected and analyzed to arrive at the overall size of the rockets and missiles market, which was further validated by primary respondents.
Secondary research was primarily used to obtain critical information about the value and supply chain of the market. It was also used to identify key players by various products, market classifications, and segmentation per their offerings. Secondary information helps understand industry trends related to defense cybersecurity offering, application, security type, end user and regions, and developments from the market and technology-oriented perspectives.
Primary Research
In the primary research process, various sources from the supply and demand sides were interviewed to obtain qualitative and quantitative information on the market. Primary sources from the supply side included industry experts such as vice presidents, directors from business development, marketing, and product development/innovation teams, related key executives from the cyber industry, defense cybersecurity solution providers, integrators, and key opinion leaders. Extensive primary research was conducted after obtaining information about the current scenario of the defense cybersecurity market through secondary research. Several primary interviews were conducted with the market experts from the demand and supply sides across major countries of North America, Europe, Asia Pacific, the Middle East, and Rest of the World (RoW).
This primary data was collected through questionnaires, emails, and telephonic interviews.
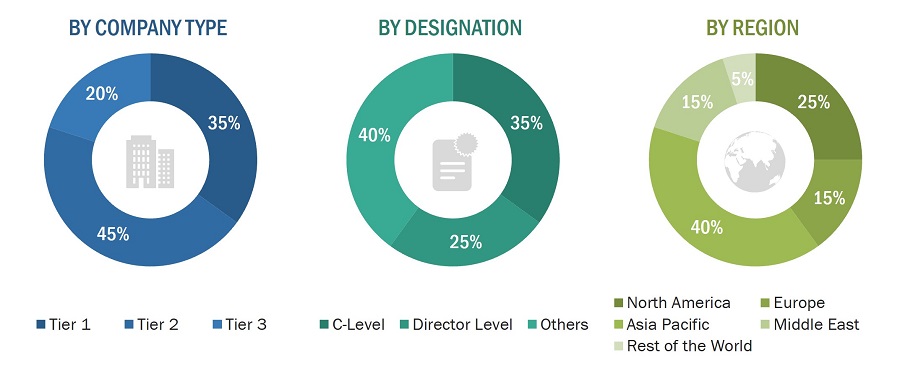
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Both the top-down and bottom-up approaches were used to estimate and validate the size of the defense cybersecurity market. The following figure represents the overall market size estimation process employed for this study on the market.
The research methodology used to estimate the market size included the following details:
-
Secondary research identified key players in the defense cybersecurity market, and their market share was determined through primary and secondary research. This included a study of annual and financial reports of top market players and extensive interviews of leaders such as CEOs, directors, and marketing executives of leading companies operating in the market.
-
All percentage shares, splits, and breakdowns were determined using secondary sources and verified through primary sources.
-
All possible parameters that affect the markets covered in this research study were accounted for, viewed in extensive detail, verified through primary research, and analyzed to obtain the final quantitative and qualitative data on the rocket and missile market.
This data was consolidated, enhanced with detailed inputs, analyzed by MarketsandMarkets, and presented in this report.
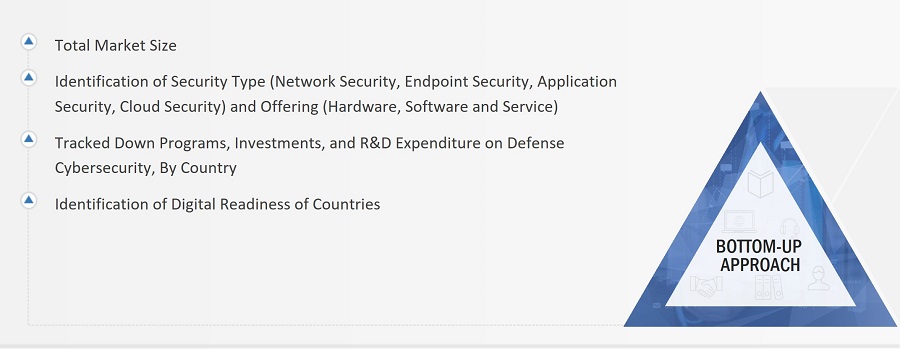
Bottom-Up Approach
The study analyzed the defense cybersecurity programs of multiple countries to understand various schemes and funding allocations for defense cybersecurity. After this, each program and its spending on procurement were tracked. For example, Booz Allen Hamilton Inc. (US) received an investment worth USD 1.86 Billion for the development of Zero Trust Network for the Defense Information Systems Agency (DISA), US. The above data was further refined by tracking various developments, such as contracts related to the upgrade of existing fleets, procurement of new platforms, and product development issued by the defense departments. The data sources considered for the market estimation and forecasting include the US DoD budget, cybersecurity development and integration, defense program publications, defense insights and data by SIPRI, defense expenditure of countries, and conflicts and geopolitical factors.
The bottom-up approach was employed to arrive at the overall size of the defense cybersecurity market from the revenues of key players and their shares in the market. Calculations based on the revenues of key players identified in the market led to the overall market size. The bottom-up approach was also implemented for data extracted from secondary research to validate the market segment revenues obtained. The market shares were then estimated for each company to verify the revenue shares used earlier in the bottom-up approach. With the data triangulation procedure and data validation through primaries, the overall parent market size and each individual market size were determined and confirmed in this study.
The bottom-up approach, employed to determine the overall size of the defense cybersecurity market, is delineated below.
Step 1:
-
Identifying top countries based on defense cybersecurity programs and budget spending
-
Identifying defense cybersecurity investments for top countries
Step 2:
-
Identifying whether defense cybersecurity considered in the scope is used or not for the top countries
-
Identifying the use of defense cybersecurity by various industries
Step 3:
-
Selecting the top countries based on their military spending
-
Developing a matrix for rating these countries on the basis of the following factors
-
MTCR Member Country
-
Defense Budget
-
Warfare Platform
-
NATO Member Country
-
Development Index
-
Conflicts & Geopolitics
-
Rating the selected countries for each parameter to determine the overall rating
-
Grouping the countries based on the overall rating synergy for correlation analysis
Step 4
-
Adding the data to the matrix after calculating the market size for the selected countries
-
Establishing a relation between the derived market size and the program spending and development of respective countries to arrive at a percentage
Step 5
-
Validating the data with the supply-side analysis by identifying the product revenue during the last five years
In September 2023, the UK Ministry of Defence awarded a contract worth USD 11 million to Leonardo S.p.A. (Italy) to support UK Armed Forces Cyber Operations.
Market Size Estimation Methodology: Bottom-Up Approach
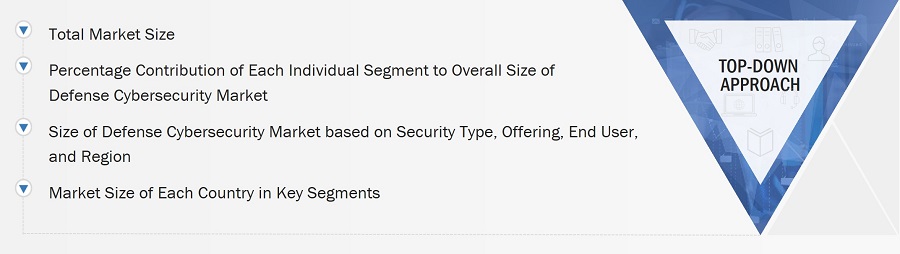
Top-Down Approach
In the top-down approach, the overall size of the defense cybersecurity market was used to estimate the size of individual markets (mentioned in the market segmentation) through percentage splits obtained from secondary and primary research. The size of the most appropriate, immediate parent market was used to implement the top-down approach to calculate the sizes of specific market segments. The approach was also implemented to validate the revenues obtained for various market segments. Market share was estimated for each company to verify the revenue share used earlier in the bottom-up approach. With the data triangulation procedure and data validation through primaries, this study determined and confirmed the overall size of the parent market and each market segment. The following figure shows the overall market size estimation process employed for this study.
Market Size Estimation Methodology: Top-Down Approach
Data Triangulation
After arriving at the overall size of the defense cybersecurity market from the market size estimation process explained above, the total market was split into several segments and subsegments. The data triangulation and market breakdown procedures explained below were implemented, wherever applicable, to complete the overall market engineering process and arrive at the estimated sizes of different market segments and subsegments. The data was triangulated by studying various factors and trends from both the demand and supply sides. Additionally, the market size was validated using both the top-down and bottom-up approaches.
The following figure indicates the market breakdown structure and the data triangulation procedure implemented in the market engineering process to develop this report.
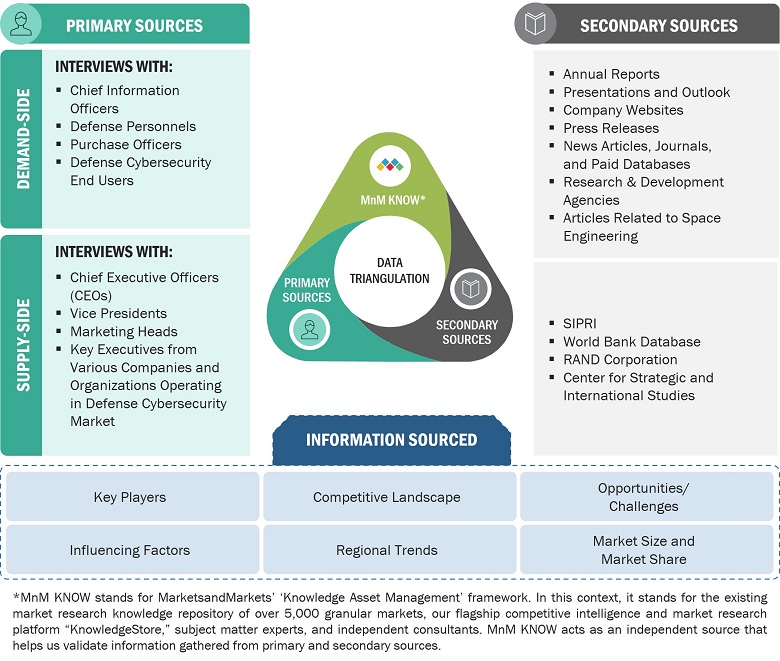
The figure above demonstrates the core data triangulation procedure used in this report for every market, submarket, and subsegment. The percentage splits of various market segments, including offering and security type, were used to determine the size of the defense cybersecurity market.
Market Definition
Defense cybersecurity, often referred to as the field of military and national security cyber defense, encompasses the strategies, technologies, and practices employed to safeguard a nation’s military and critical infrastructure from cyber threats and attacks. Defense cybersecurity focuses on countering a wide range of cyber adversaries, including state-sponsored actors, hacktivists, and criminal organizations, who seek to compromise sensitive government systems, military operations, and essential infrastructure like power grids, transportation networks, and financial institutions.
Defense cybersecurity solutions encompass a spectrum of measures, including intrusion detection, threat intelligence, encryption, secure communication protocols, and the development of resilient infrastructure that can withstand cyberattacks. The defense cybersecurity market involves government agencies, private defense contractors, cybersecurity companies, research institutions, and international collaborations, all working together to stay ahead of evolving threats and protect national security interests.
Key Stakeholders
-
Aerospace & Defense Companies
-
Space Industry Players
-
Research Institutions and Universities
-
Testing and Certification Organizations
-
Material and Technology Providers
-
Investors and Financial Institutions
-
Regulatory Bodies
Report Objectives
-
To define, describe, and forecast the size of the defense cybersecurity market based on security type, end user offering, application, and region from 2023 to 2028
-
To forecast the size of market segments with respect to major regions, namely North America, Europe, Asia Pacific, Middle East, and the Rest of the World (RoW) Africa & Latin America
-
To identify and analyze key drivers, restraints, opportunities, and challenges influencing the growth of the global defense cybersecurity market
-
To strategically analyze micromarkets1 with respect to individual growth trends, prospects, and their contribution to the defense cybersecurity market
-
To analyze opportunities for stakeholders in the defense cybersecurity market by identifying key market trends
-
To analyze competitive developments such as contracts, acquisitions and expansions, agreements, partnerships, product launches, and research & development (R&D) activities in the defense cybersecurity market
-
To provide a detailed competitive landscape of the -market, in addition to an analysis of business and corporate strategies adopted by leading market players
-
To strategically profile key market players and comprehensively analyze their core competencies
To strategically profile key market players and comprehensively analyze their core competencies2
1. Micro markets refer to further segments and subsegments of the hypersonic flight market included in the report.
2. The core competencies of the companies were captured in terms of their key developments and strategies adopted by them to sustain their position in the market.
Available customizations
Along with the market data, MarketsandMarkets offers customizations as per the specific needs of companies. The following customization options are available for the report:
Product Analysis
-
Product matrix, which gives a detailed comparison of the product portfolio of each company
Regional Analysis
-
Further breakdown of the market segments at the country level
Company Information
-
Detailed analysis and profiling of additional market players (up to 5)



Growth opportunities and latent adjacency in Defense Cybersecurity Market