Vendor Comparison in Mobile Application Security, 2015 – MnM DIVE Matrix
In today’s hyper-connected business environment, organizations are exploring ways to enhance functionalities to mobile devices enabling access to business critical information from anywhere, at any time. This makes mobile platform an increasingly attractive security target.
MarketsandMarkets defines mobile application security as the comprehensive security approach to ensure the confidentiality of the data transferred among mobile applications, while ensuring transparency and visibility among business processes.
Mobile application security solutions empower IT security teams to rapidly secure mobile applications from potential threats and risks, through various testing capabilities, such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST). This involves examining the structure of mobile applications and studying how they exchange data in a cohesive manner, as well as identifying the key patches which can be easily exploited by hackers for financial gains. The key functionalities covered by mobile application security include threat mitigation, source code review, behavioral analysis, identification of vulnerability patterns, vulnerability ratings, and risk analysis.
Vendor Inclusion Criteria
We have selected 10 vendors for evaluations based on their breadth of product offering and robust business strategy. The focus of our vendor evaluation is based on the product they offer in the mobile application security market. A comprehensive list of all the vendors in this market was created through a product mapping strategy and MarketsandMarkets analysis. Based on their capabilities, innovations, and breadth of product offering, vendors were shortlisted. Our selected vendor mix includes companies from Tier 1 to Tier 4 and covers the whole market comprehensively. The below table describes the company type with their revenue range:
|
Company type |
Revenue range |
|
Tier 1 |
More than USD 10 billion |
|
Tier 2 |
USD 1 billion–USD 10 billion |
|
Tier 3 |
USD 1 billion–USD 500 million |
|
Tier 4 |
Less than USD 500 million |
The report excludes vendors that offer only services in the mobile application security space, such as Intel Security (McAfee), Trustwave, MobileIron, and others.
Vendors Evaluated
The report covers the comprehensive study of the key vendors offering solutions for mobile application security. We have evaluated the following 10 vendors: Appthority, Arxan Technologies, Cigital, Checkmarx, IBM Corporation, HP, Pradeo, Rapid7, Veracode, and WhiteHat Security.
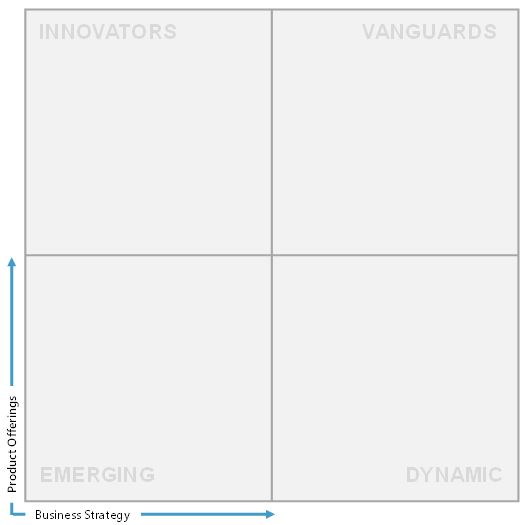
The Vendor DIVE Matrix will look like as below:
To know about the Vendor DIVE, download the pdf brochure
Customer Interested in this report can also view
Mobile Application Security Market by Solution (Antivirus & Antitheft, Data Recovery and Others), Deployment Type (Cloud & On Premise), User Type, Industry Vertical (BFSI, Healthcare & Others) and by Region - Global Forecast to 2020
Mobile application security provides detailed security analysis of mobile-based applications. It includes custom scans and in-depth vulnerability checks through various testing capabilities, such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST). Mobile application security empowers the IT security team to identify critical application risks and enables them to rapidly secure mobile applications from potential threats.
The consumerization of IT and the trend of Choose Your Own Device (CYOD) are disrupting the way enterprises and employees access corporate networks and resources and are continuously evolving over time. This risk of exposure of critical organizational data has pushed the enterprises to deploy mobile application security solutions to ensure security of their confidential data as well as secure the process of data exchange among applications.
MarketsandMarkets Vendor DIVE, Q4 2015 reviews major players that offer mobile application security solutions and outlines the findings and analysis on the basis of their product offerings and business strategies. The vendor evaluations are based on two broad categories: Product Offering and Business Strategy. Each category carries various criteria, based on which the vendors are evaluated. The criteria are provided below:
|
Product Offering |
Business Strategy |
|
Breadth of Offering |
Reach |
|
Feature/Functionality |
Industry Coverage |
|
Delivery |
Channel |
|
Scalability |
Viability |
|
Support |
Roadmap |
|
|
Inorganic Growth |
Based on the extensive secondary and primary research, key information about the vendor’s product offering and business strategies was gathered. After the completion of data gathering and verification process, the scores and weightage for shortlisted vendors against each parameter was finalized. After evaluating all the vendors, a comparison scorecard was prepared and each vendor was placed in the Vendor DIVE Matrix based on their product offering and business strategy scores.
This report is instrumental in helping the stakeholders, such as mobile application security vendors, system integrators, value-added resellers, and technology partners, to make business decisions on mobile application security solution deployments.
The report covers the comprehensive study of mobile application security vendors, including Appthority, Arxan Technologies, Cigital, Checkmarx, IBM Corporation, HP, Pradeo, Rapid7, Veracode, and WhiteHat Security.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst

Table of Contents
1 Develop, Deliver, and Deploy Secure Mobile Apps for an Enriched End-User Experience
2 Mobile Application Security: Best Practices
3 DIVE Evaluations
3.1 Vendor Inclusion Criteria
3.2 Vendors Evaluated
3.3 DIVE Evaluation Overview
4 Vendor Profiles
4.1 IBM Corporation
4.2 Hewlett-Packard (HP)
4.3 Pradeo Security Systems
4.4 WhiteHat Security
4.5 Checkmarx
4.6 Veracode
4.7 Rapid7
4.8 Arxan Technologies
4.9 Appthority
4.10 Cigital
5 Supplemental Materials
5.1 Vendor DIVE Methodology
5.2 Quadrant Description
5.3 Related Research
6 Endnotes













Growth opportunities and latent adjacency in Vendor Comparison in Mobile Application Security, 2015