Hardware Encryption Market Size, Share, Trends & Industry Growth Analysis Report by Product Type (External HDD, Internal HDD, SSD, Inline Network Encryptor, USB Flash Drive), Application (Consumer Electronics, Aerospace & Defense, Transportation, Healthcare) and Region – Forecast to 2027
Updated on : Oct 23, 2024
Hardware Encryption Market Size & Growth
The global hardware encryption market size is expected to reach USD 357 million by 2027, growing at a CAGR of 4.8% during the forecast period. The growth of this market is driven by factors such as compliance with data privacy security regulations and standards, increasing apprehension over data security and confidentiality, and development of digital content.
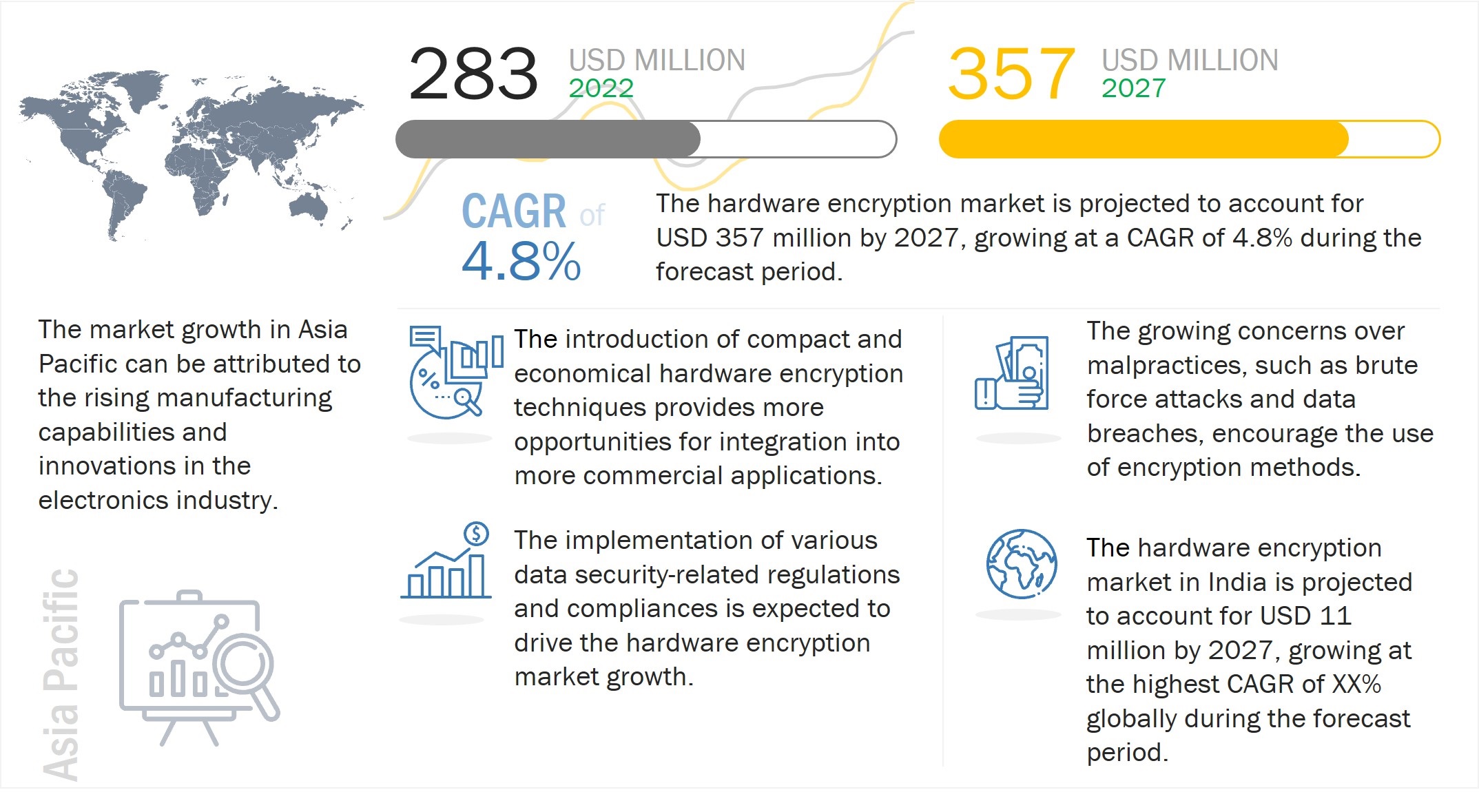
Hardware Encryption Market Forecast to 2027
To know about the assumptions considered for the study, Request for Free Sample Report
Hardware Encryption Market Dynamics
Drivers: Development of digital content
With the emergence of the smart city concept worldwide, the use of information and communications has become more digitalized, leading to the enhancement of digital content. The concept of smart cities includes smart transport, smart energy, smart water, and smart healthcare. These smart cities use various IoT technologies such as radio-frequency identification (RFID) sensors, cloud computing, and wireless networks to gather and analyze information about environmental factors, transportation, water supply, public safety, and hospitals to enhance the quality of life.
Thus, with the emergence of smart cities, there is a growing concern over data loss and the exchange of secure information or storage. Digital content is expanding globally, and the Internet era is evolving with the introduction and adoption of cloud computing, IoT, big data analytics, and others. Also, the increasing adoption of smartphones, e-cash, e-tailing, video surveillance, and digital marketing is further adding to the expansion of digital content. Continuous technological advancements and the introduction and application of IoT in the present lifestyle have significantly enhanced digital content. Data has become the currency of the new economy. With increasing flexibility becoming available in the usage and storage of data, the need for secured storage and hardware encryption to protect against cyberattacks, online spying, cyber espionage, and other security-related threats is growing. Thus, the expansion and management of digital content are driving the growth of the hardware encryption industry.
Restraints: Heavy capital investments by stakeholders
Substantial capital investments are required for the installation and maintenance of hardware-based encryption technology. This type of encryption involves the installation of encryption under HDDs to ensure a high level of protection. It comprises installing a dedicated network platform to protect various storage systems, desktops, laptops, and tablets.
It also involves the installation of firmware and cryptographic processors into the devices, along with the use of algorithms and standards and architectures. The total installation cost of installing hardware encryption technology includes licensing cost, annual maintenance cost, OPAL fees, pre-provisioning cost, staging cost, the technical cost for a password reset, user idle time cost for encryption, user excess operating cost, and technical cost for the assistance of expert administration of encrypted drives. However, hardware-based encryption is gaining traction with the growing concern over secure data storage. Players in the hardware encryption market are launching economic products, because of which the average cost of a single hardware-encrypted device has begun declining. Technological innovations have also helped reduce the average cost of installing hardware encryption. Also, with rapid technological advancements, the impact of high capital investments is reducing at a fast pace but needs to be reduced much more for it to no longer remain an impediment to the growth of the market.
Opportunities: Substantial development and growth of IoT in various industries
IoT has witnessed significant technological innovation and commercialization in all fields. IoT is used in day-to-day activities with its commercialized application in agriculture, consumer electronics, transportation, military and defense, telecommunications, medical, energy, finance, and aerospace. IoT also plays an integral part in various emerging concepts, such as smart cities, digital marketing, and others.
IoT demands large-scale management and protection of digital certificates and the underlying keys and supports multiple public-key algorithms, including Elliptic Curve Crypto (ECC), whose shorter key lengths and less intensive computational power are well suited for constrained IoT devices, all supported by a well-designed public key infrastructure (PKI). The accepted PKI best practice to secure the most sensitive keys and business processes is to use an HSM.
IoT involves the interaction between M2M and machine-to-humans, -objects, -environment, and -infrastructure. IoT devices are used to monitor machinery, employees, and environmental conditions in power stations, network gateways, avionics, wireless base stations, and others. The data acquired helps analyze, control, prevent risks, avoid economic losses, and assist in effective and efficient decision-making.
Since IoT finds applications across all sectors, it is exposed to various threats, such as unauthorized use and data manipulation. For instance, following the introduction of 4G LTE mobile networks, automobiles use IoT to provide real-time information on traffic conditions, navigation services, remote engine start facilities, and other related services. In this case, any manipulation or unauthorized use of data can cause accidents and traffic outrage. Thus, the increasing adoption of IoT devices in various fields is driving the need to protect data at all levels and provide end-to-end encryption to secure the exchange of information. Thus, the commercialization of IoT is providing a growth opportunity for the hardware encryption market.
Challenges: Adoption of SED and TPM in current processors
Strong user authentication is critical for better security. With a Software Encryption Drive (SED), access to the platform is based on secure authorization from the SED and not by the software that can be fooled into allowing unauthorized access to data. Mixing hardware-based encryption with Trusted Platform Modules (TPMs) can provide even stronger security benefits. By combining hardware-based technologies such as SEDs with TPMs, enterprises add another layer of security to their systems, ensuring that the possibility of any loss of data is drastically reduced. Clients prefer SEM and TPM over hardware encryption considering the security benefits and less hardware equipment, which helps in space optimization.
Hardware Encryption Industry Overview
Hardware Encryption Market Analysis
Hardware Encryption Market Trends
Hardware Encryption Market Share
Consumer Electronics is expected to hold the largest share of hardware encryption market for during the forecast period
The market for consumer electronics application segment accounted for the largest share of ~41% of the market in 2021 and is expected to retain its position as the highest during the forecast period from 2022 to 2027. Hardware encryption is used in electronic devices such as desktops, smartphones, notebooks, laptops, and tablets, among others.
All electronic equipment with digital storage, either magnetic or solid-state, can have hardware encryption enabled. The products mostly used for hardware encryption in consumer electronic devices include SSDs and HDDs. This is attributed to the emergence of bring-your-own-devices (BYOD) across several organizations and other consumer electronic devices such as laptops, tablets, and smartphones, which is expected to generate the need for hardware-encrypted security.
Hardware Encryption Market - Regional Analysis
Asia Pacific to hold the largest share of hardware encryption market for in 2022
The market in Asia Pacific holds the largest market share and is expected to retain its position during the forecast period growing at the highest CAGR of 5.5% from 2022 to 2027. The growth of the market in this region can be attributed to the emergence of several manufacturers of electronic devices in the region, along with the expansion of IT and telecom networks in China, South Korea, India, and other emerging economies of the region.
Asia Pacific is a hub for several companies manufacturing consumer electronics, such as smartphones, as well as providers of advanced ICT technologies. Companies in Asia Pacific are adopting hardware encryption technology for data security and protection. Moreover, the significant number of ongoing smart city projects in the countries of the region is also expected to fuel the growth of the hardware encryption market in Asia Pacific during the forecast period.
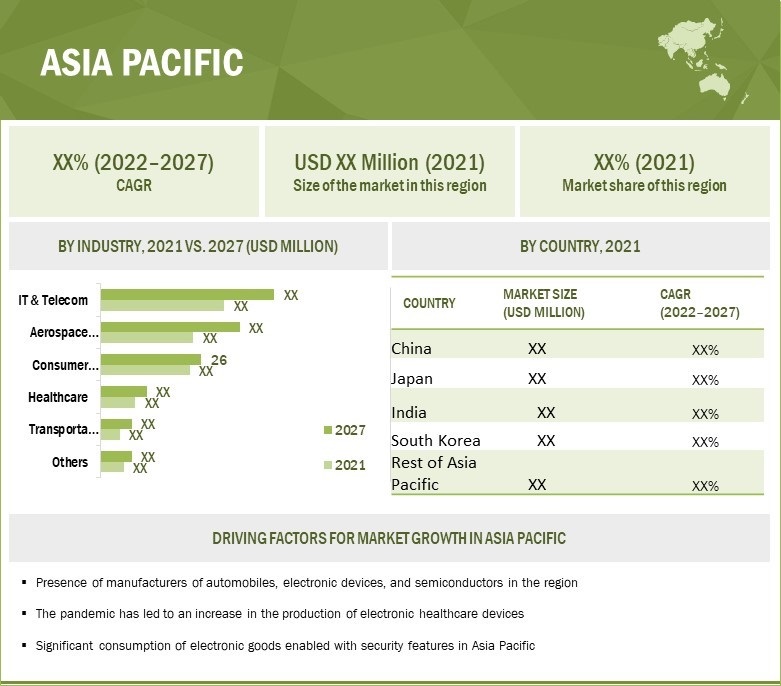
Hardware Encryption Market by Region
To know about the assumptions considered for the study, download the pdf brochure
Top Hardware Encryption Companies - Key Market Players
Some of the key hardware encryption companies are include Western Digital Technologies, Inc. (US), Samsung Electronics Co., Ltd. (South Korea), Micron Technology, Inc. (US), Kingston Technology Corporation (US), Seagate Technology Holdings PLC (US), NetApp, Inc. (US), KIOXIA Holdings Corporation (Japan), Kanguru Solutions (US), Intel Corporation (US), WinMagic Inc. (Canada), Maxim Integrated Products, Inc. (US), Thales e-Security, Inc. (US), McAfee, LLC (US), and so on.
Hardware Encryption Market Report Scope
|
Report Metric |
Details |
|
Estimated Market Size
|
USD 271 million |
| Projected Market Size | USD 357 million |
| Hardware Encryption Market Growth Rate | CAGR of 4.8% |
|
Years Considered |
2022–2027 |
|
Base Year |
2021 |
|
Forecast Period |
2022–2027 |
|
Forecast Units |
Value (USD Million) |
|
Segments Covered |
Architecture, Product, Application, and Geography |
|
Geographies Covered |
North America, Europe, Asia Pacific, and RoW |
|
Companies Covered |
Western Digital Technologies, Inc. (US), Samsung Electronics Co., Ltd. (South Korea), Micron Technology, Inc. (US), Kingston Technology Corporation (US), Seagate Technology Holdings PLC (US), NetApp, Inc. (US), KIOXIA Holdings Corporation (Japan), Kanguru Solutions (US), Intel Corporation (US), WinMagic Inc. (Canada), Maxim Integrated Products, Inc. (US), Thales e-Security, Inc. (US), McAfee, LLC (US), Broadcom Inc. (US), International Business Machines Corporation (US), etc. Total 25 Major Players |
Hardware Encryption Market Highlights
In this research report, the market has been segmented based on Architecture, Product, Application, and Geography.
|
Aspect |
Details |
|
Hardware Encryption Market, by Architecture: |
|
|
Market, by Product: |
|
|
Market, by Application: |
|
|
Geographic Analysis: |
|
Recent Developments in Hardware Encryption Industry
- In May 2022, Western Digital Technologies, Inc. (US) and Kioxia Holdings Corporation (Japan) entered an agreement to jointly invest in the first phase of the Fab7 (Y7) factory at Kioxia’s Yokkaichi Plant campus in the Mie Prefecture of Japan. Y7 is the sixth flash memory factory at the Yokkaichi Plant campus, which is one of the world’s largest flash memory manufacturing sites. The first phase of the Y7 facility will produce 3D flash memory devices, including 112- and 162-layer nodes.
- In May 2022, Micron Technology, Inc. announced the upcoming availability of two new consumer storage products, the Crucial P3 Plus Gen4 NVMe and Crucial P3 NVMe solid-state drives (SSDs), as an expansion of its Crucial NVMe SSD product portfolio. The new Crucial P3 Plus SSD product line will deliver sequential read/write speeds up to 5000/4200 MB/s1, while next-generation Crucial P3 SSDs will provide read/write speeds up to 3500/3000 MB/s1.
- In March 2021, Samsung Electronics Co., Ltd. (South Korea) launched 980NVMe, a new addition to the SSD portfolio, the company’s first consumer drive without DRAM, with more speed and access to a wider range of users.
Frequently Asked Questions (FAQs):
What is the current size of the global Hardware encryption market?
The global hardware encryption market was valued at USD 271 million in 2021 and is expected to grow at a CAGR of 4.8% from 2022 to reach USD 357 million by 2027.
Who are the winners in the global Hardware encryption market?
Some of the key companies operating in the Hardware encryption market are Western Digital Technologies, Inc. (US), Samsung Electronics Co., Ltd. (South Korea), Micron Technology, Inc. (US), Kingston Technology Corporation (US), Seagate Technology Holdings PLC (US), NetApp, Inc. (US), KIOXIA Holdings Corporation (Japan), Kanguru Solutions (US), Intel Corporation (US), WinMagic Inc. (Canada), Maxim Integrated Products, Inc. (US), Thales e-Security, Inc. (US), McAfee, LLC (US), Broadcom Inc. (US), and so on. These players have adopted various growth strategies such as product launches/developments, partnerships/contracts/ collaborations/acquisitions to expand their global presence and increase their share in the global Hardware encryption market.
What are the major drivers for the Hardware encryption market?
The growth of this market is driven by factors such as compliance with data privacy security regulations and standards, increasing apprehension over data security and confidentiality, and development of digital content.
What are the growing application verticals in the Hardware encryption market?
The market for consumer electronics application segment accounted for the largest share of ~41% of the hardware encryption market in 2021 and is expected to retain its position as the highest during the forecast period from 2022 to 2027.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst

The study involved 4 major activities in estimating the size of the hardware encryption market. Exhaustive secondary research was done to collect information on the market. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain through primary research. Both top-down and bottom-up approaches were employed to estimate the total market size. Further, market breakdown and data triangulation were used to determine the market sizes of segments and subsegments.
Secondary Research
The secondary sources referred to for this research study include organizations such as Semiconductor Industry Association, Global Association of Risk Professionals, Storage Networking Industry Association (SNIA), IEEE, Electronics Representatives Association, Institute of Information Engineering, CAS, and so on; corporate filings (such as annual reports, investor presentations, and financial statements); and trade, and business. Secondary data has been collected and analyzed to determine the overall market size, further validated by primary research.
Primary Research
Extensive primary research has been conducted after acquiring an understanding of the hardware encryption market scenario through secondary research. Several primary interviews have been conducted with market experts from both the demand- (commercial application providers) and supply-side (equipment manufacturers and distributors) players across four major regions, namely, North America, Europe, Asia Pacific, and Rest of the World (South America, Middle East & Africa). Approximately 75% and 25% of primary interviews were conducted from the demand and supply sides, respectively. Primary data has been collected through questionnaires, emails, and telephonic interviews. In canvassing primaries, various departments within organizations, such as sales, operations, and administration, were covered to provide a holistic viewpoint in our report.
After interacting with industry experts, brief sessions were conducted with highly experienced independent consultants to reinforce the findings from the primaries. This, along with the in-house subject matter experts’ opinions, has led us to the findings described in the remainder of this report.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Both top-down and bottom-up approaches were used to estimate and validate the total size of the hardware encryption market. These methods were also extensively used to estimate the sizes of various market subsegments. The research methodology used to estimate the market sizes includes the following:
- The key players in the market were identified through extensive secondary research.
- In terms of value, the supply chain and market size were determined through primary and secondary research.
All percentage shares, splits, and breakdowns were determined using secondary sources and verified through primary sources. Qualitative aspects such as market drivers, restraints, opportunities, and challenges have been considered while calculating and forecasting the market size.
Global Hardware Encryption Market Size: Bottom-Up Approach
Data Triangulation
After arriving at the overall market size-using the market size estimation processes explained above-the market was split into several segments and sub-segments. Data triangulation and market breakdown procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Report Objectives:
- To describe and forecast the global hardware encryption market based on architecture, product, application, and region, in terms of value.
- To describe and forecast the market for four main regions: North America, Europe, Asia Pacific, and Rest of the World (RoW), in terms of value.
- To provide detailed information regarding drivers, restraints, opportunities, and challenges influencing the growth of the market
- To provide a detailed overview of the value chain pertaining to the ecosystem of the market
- To strategically analyze micromarkets1 with respect to individual growth trends, prospects, and contributions to the total market
- To analyze opportunities in the market for various stakeholders by identifying high-growth segments
- To benchmark players within the market using the proprietary competitive leadership mapping framework, which analyzes market players using various parameters within the broad categories of business and product strategy
- To strategically profile key players and comprehensively analyze their market position in terms of ranking and core competencies2, along with detailing the competitive landscape for market leaders
- To analyze competitive developments such as acquisitions, product launches and developments, and research and developments in the market
1. Micromarkets are defined as the further segments and subsegments of the hardware encryption market for the abovementioned applications.
2. Core competencies of companies are defined in terms of their key developments and key strategies adopted to sustain their position in the market.
Customization Options:
With the given market data, MarketsandMarkets offers customizations according to the company’s specific needs. The following customization options are available for the report:
Company Information
- Detailed analysis and profiling of additional market players (up to 5)


 Generating Response ...
Generating Response ...










Growth opportunities and latent adjacency in Hardware Encryption Market