Vendor Comparison in Identity and Access Management – 2017: MnM DIVE Matrix
[102 Pages Report] In today’s technology environment, cyber threats and vulnerabilities have become a boardroom discussion in organizations across the globe. The need to mitigate IT security risks and protect data, applications, and various endpoints against threats are still the primary goal of organizations. Identity and Access Management (IAM) can be described as the management of individual identities, their authorization, and provision of access, based on predefined rules.
MarketsandMarkets defines identity and access management as a business security framework that manages digital identities scattered both inside and outside the enterprises. IAM solutions manage the access to information and applications across enterprises by undertaking security and risks considerations. These solutions facilitate enterprises to create, store, delete, and maintain user identities and their related access permissions, automatically. Thus, it enables individuals to access the right resources at the right time.
Growing emphasis on compliance management and increasing trend of mobility has led to the rising demand for IAM solutions in various sectors. The workforce has become more mobile these days; moreover, Bring Your Own Device (BYOD) approach is increasing the usage of mobile applications. Furthermore, the prevalent surge in e-commerce and consumer demand for mobile computing is also motivating organizations to develop mobile applications that are used by the customers to access their products. These changing scenarios and distributed IT environments have made organizations susceptible to cyber threats, hence fueling the demand for IAM solutions. This is expected to create lucrative market opportunities for the IAM vendors during the forecast period.
This report on vendor comparison in identity and access management based on MNM DIVE methodology analyzes and evaluates the key vendors in the IAM market.
To know about the assumptions considered for the study, download the pdf brochure
Vendor Inclusion Criteria
We have selected 25 vendors for evaluations based on their breadth of product offering and robust business strategy. The focus of our vendor evaluation is based on the product they offer in the identity and access management market. A comprehensive list of all the vendors in this market was created through a product mapping strategy and MarketsandMarkets analysis. Based on their capabilities, innovations, and breadth of product offering, vendors were shortlisted. Our selected vendor mix includes top 25 IAM vendors selected, based on the above given parameters.
Vendors Evaluated
The report covers comprehensive study of the key vendors offering solutions for IAM. We have evaluated the following 25 vendors: Avatier Corporation, Bitium, Inc. , Beta Systems, CA Technologies, Centrify Corporation, Covisint Corporation, Crossmatch, Dell Software, ForgeRock, Gemalto N.V., Hitachi ID Systems, IBM Corporation, Ilantus Technologies, iWelcome, Microsoft Corporation, Micro Focus, Okta, Inc., Omada A/S, OneLogin, Inc., Oracle Corporation, Ping Identity, SailPoint, Simeio Solutions, Salesforce.com, Inc., and UXP Systems.
The MNM DIVE matrix will look like as below:
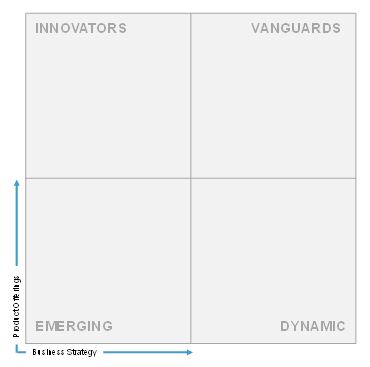
Identity and Access Management (IAM) is a business security framework that manages digital identities scattered both inside and outside the enterprises. IAM solutions manage the access to information and applications across enterprises by undertaking security and risks considerations. These solutions facilitate enterprises to create, store, delete, and maintain user identities and their related access permissions, automatically. Thus, it enables individuals to access the right resources at the right time.
Lack of IAM in the organizations may pose a significant threat to compliance and security in general. To mitigate these threats, companies are adopting IAM solutions, which help in identity management, password & access authentication, synchronizing identities between directories, access to sensitive enterprise applications, and data on users’ preferred mobile devices. These solutions not only provide highly secured environment but are also economical in terms of time and cost, operational efficiency, and management control.
The report on vendor comparison in IAM based on MarketsandMarkets DIVE methodology reviews major players that offer IAM solutions and outlines the findings and analysis on the basis of two broad categories: product offerings and business strategies. Each category carries various criteria, based on which, the vendors are evaluated. The criteria are provided below:
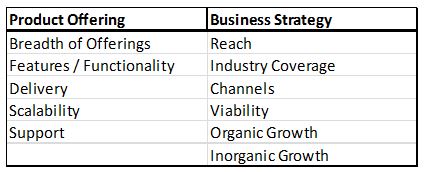
Based on the extensive secondary and primary research, key information about the vendors’ product offerings and business strategies was gathered. After the completion of data gathering and verification process, the scores and weightage for shortlisted vendors against each parameter were finalized. A comparison scorecard was prepared after evaluating all the vendors, and each vendor was placed in the MNM DIVE matrix on the basis of their product offering and business strategy scores.
This report is instrumental in helping the stakeholders, such as IAM solution vendors, cyber security vendors, cloud service providers, system integrators, value-added resellers, and other channel partners, to make business strategies and decisions on the deployment of IAM solutions.
The report covers the comprehensive study of key IAM vendors, including Avatier Corporation, Beta Systems, Bitium, Inc., CA Technologies, Centrify Corporation, Covisint Corporation, Crossmatch, Dell Software, ForgeRock, Gemalto N.V., Hitachi ID Systems, IBM Corporation, Ilantus Technologies, iWelcome, Microsoft Corporation, Micro Focus, Okta, Inc., Omada A/S, OneLogin, Inc., Oracle Corporation, Ping Identity, SailPoint, Simeio Solutions, Salesforce.com,Inc., and UXP Systems.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst

Table of Contents
Introduction
About the Document
Market Definition
Stakeholders
Premium Insights
MnM Dive Overview
Dive Evaluation Criteria
Vendor Inclusion Criteria
Vendors Evaluated
MnM Voice: Identity and Access Management
Identity and Access Management: A Framework That Grants the Right Access to the Right Person at the Right Time for Information Technology Resources
Identity and Access Management: Best Practices
Identity and Access Management: Vendor Comparison
MnM Dive Vendor Comparison Scorecard
MnM View
Vendor Profiles
(Business Overview, Products & Services, Key Insights, Recent Developments, SWOT Analysis, MnM View)*
Avatier Corporation
Beta Systems
Bitium, Inc.
Ca Technologies
Centrify Corporation
Covisint Corporation
Crossmatch
Dell Software
Forgerock
Gemalto N.V.
Hitachi ID Systems, Inc.
IBM Corporation
Ilantus Technologies
Iwelcome
Microsoft Corporation
Micro Focus
Okta, Inc.
Omada A/S
Onelogin, Inc.
Oracle Corporation
Ping Identity
Sailpoint
Simeio Solutions
Salesforce.Com, Inc.
UXP Systems
*Details on Business Overview, Products & Services, Key Insights, Recent Developments, SWOT Analysis, MnM View Might Not Be Captured in Case of Unlisted Companies.
Appendix
MnM Dive: Vendor Comparison Methodology
Matrix Description
List of Abbreviations
Related Reports
Author Details













Growth opportunities and latent adjacency in Vendor Comparison in Identity and Access Management