Security Automation Market by Offering (Solutions, Services), Code Type, Technology (AI & ML, Predictive Analytics), Application (Network Security, IAM), Vertical (BFSI, Manufacturing, Media & Entertainment) and Region - Global Forecast to 2028
Updated on : Jan 27, 2026
Security Automation Market - Worldwide | Future Scope & Trends
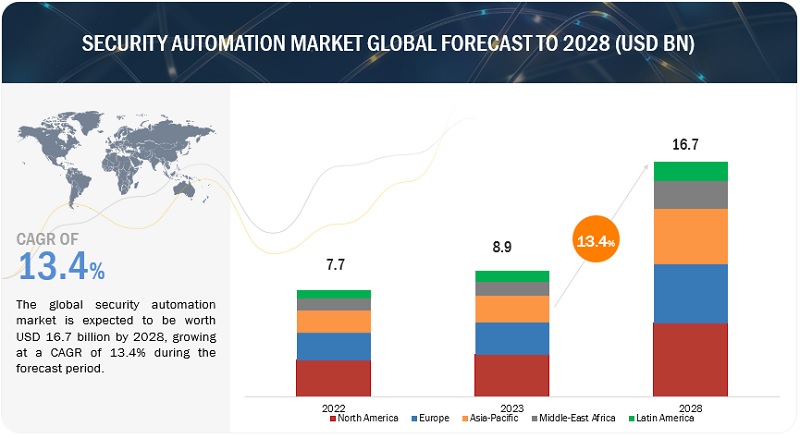
The global security automation market size was valued at USD 8.9 billion in 2023 and is expected to grow at a CAGR of 13.4% from 2023 to 2028. The revenue forecast for 2028 is projected to reach $16.7 billion. The base year for estimation is 2022, and the historical data spans from 2023 to 2028.
Due to various business drivers, the security automation market is expected to grow significantly during the forecast period. The market is experiencing significant growth due to the increasing incidents of phishing emails and ransomware, and need to ensure consistent adherence to security policies and facilitates audit trails. The rising cybersecurity threats and complexity, growing ability to detect and respond to security incidents in real-time is also responsible for driving the market’s growth.
To know about the assumptions considered for the study, Request for Free Sample Report

To know about the assumptions considered for the study, download the pdf brochure
Market Dynamics
Driver: Rising cybersecurity threats and complexity
The escalating frequency and sophistication of cyber threats have created a pressing need for organizations to bolster their cybersecurity measures. The dynamic nature of modern cyberattacks, ranging from ransomware and zero-day exploits to social engineering and nation-state attacks, has led to a heightened sense of vulnerability. As threats become more complex, diverse, and targeted, traditional manual approaches to cybersecurity are often inadequate to address the rapidly evolving landscape. Security Automation plays a critical role in countering these threats by providing real-time detection, rapid response, and proactive defense mechanisms. According to the FBI's Internet Crime Report, cybercrime resulted in over USD 4.2 billion in financial losses in 2020 in the US only. The report highlighted the increasing sophistication of cybercriminal tactics across major countries. Moreover, The Verizon Data Breach Investigations Report (DBIR) consistently points out the expanding attack surface, including cloud-based threats, web application attacks, and social engineering. This necessitates a dynamic and automated defense mechanism. The increasing landscape of cybersecurity threats, marked by their complexity and variety, underscores the necessity of security automation. Automation enables organizations to detect, respond to, and mitigate threats at a pace and scale that human intervention alone cannot achieve.
Restraints: Concerns related to data privacy
The concern related to data privacy and security is a significant factor that can hamper the adoption of security automation solutions in the market. Addressing privacy concerns related to data collection, processing, and sharing requires careful consideration of legal and ethical implications, which might prolong resolution. Data privacy concerns revolve around the collection, processing, and sharing of data within automated security processes. Security automation often requires access to sensitive data for analysis and decision-making. Organizations are troubled about the unintended exposure of this data, leading to potential breaches or misuse. Moreover, automated processes might involve data transfers between systems or to external vendors. This lack of direct control over data movement raises concerns about data being mishandled or accessed without proper authorization. Addressing these concerns requires a comprehensive approach that integrates privacy by design principles into the development and deployment of security automation solutions. Organizations must conduct thorough privacy impact assessments, implement data protection safeguards, ensure encryption, and secure data handling, and stay informed about relevant data protection regulations.
Opportunity: Rise in advent of predictive analytics to anticipate potential threats
The rise in the advent of predictive analytics is a significant catalyst for the growth of security automation solutions in the market, as it empowers organizations to anticipate and counter cyber threats with unprecedented accuracy. By leveraging historical and real-time data, predictive analytics can foresee potential security breaches, vulnerabilities, and attack patterns. When integrated into security automation solutions, these predictive insights enable proactive threat mitigation, preemptive incident responses, and the optimization of security workflows. This advanced foresight enhances the effectiveness of automated processes, reducing risks, minimizing downtime, and ultimately fortifying an organization's cybersecurity posture in an increasingly dynamic threat landscape. With predictive insights, security automation can craft more tailored and context-aware responses to threats, ensuring a nuanced approach that aligns with the organization's risk tolerance and objectives. For instance, a Ponemon Institute study found that organizations that use AI in their security operations reduce the mean time to respond to an incident by 12.7% and the mean time to resolve by 11.3%. Predictive analytics empowers automated incident response with timely precision.
Challenge: Shortage of modern IT infrastructure
The shortage of modern IT infrastructure poses a significant hindrance to the growth of security automation solutions in the market. Inadequate or outdated infrastructure can limit the capabilities required to effectively implement and manage automation processes, such as real-time data processing, integration with various tools, and seamless communication between systems. Without a robust and modern IT foundation, organizations may struggle to fully leverage the potential of security automation, impeding its adoption and diminishing its ability to provide timely threat detection, response, and overall cybersecurity enhancement. Moreover, with systems becoming more dispersed, customizable, and heterogeneous, the quantity of data collected regarding security services is vast. The data collected from various components of the infrastructure keeps increasing; hence, the segregation of important data becomes a challenge for any IT department. As organizations grow, so does the volume and variety of the data that attracts even more diversified threats for which firms are unprepared. Thus, modern-day security automation vendors focus on a shared technology framework that can address such issues.
Security Automation market ecosystem

By offering, SOAR solutions segment to account for a larger market size during forecast period
The security automation solutions include SOAR solutions. SOAR solutions integrate security orchestration, automated workflows, and threat intelligence to enable more efficient and effective handling of security incidents and threats. The growth of the SOAR segment is evident in the expanding offerings of established cybersecurity vendors and the emergence of specialized startups focusing exclusively on SOAR solutions. Market reports and industry analyses consistently highlight the increasing adoption of SOAR technologies across various sectors.
By technology, predictive analytics registers the highest CAGR during the forecast period
The predictive analytics segment is projected to grow more during the forecast period. In the security automation market, predictive analytics contributes by identifying patterns and anomalies within vast datasets, thereby enabling security teams to anticipate potential breaches and vulnerabilities. Predictive analytics enhances incident response capabilities by enabling security teams to prioritize alerts based on risk levels
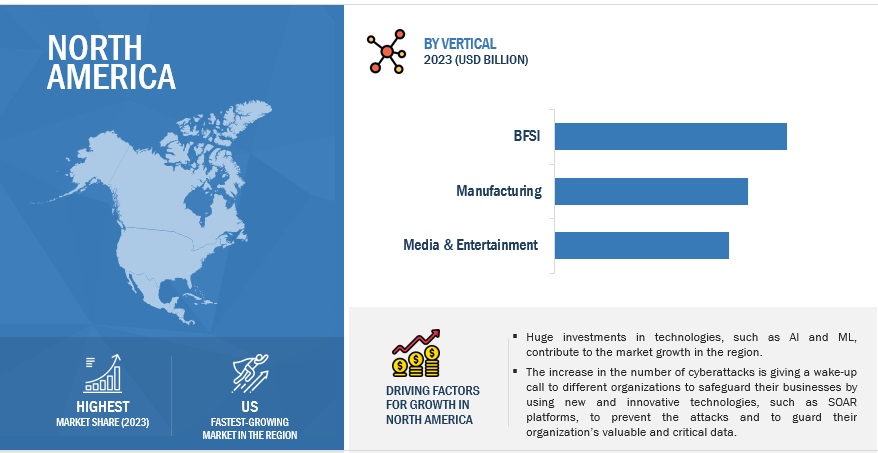
By region, North America holds the largest market size during the forecast period
North America will lead the security automation market in 2023. North America, comprising the United States and Canada, is known for its advanced technology infrastructure and innovative industries, making it a hub for adopting security automation technologies. The increase in the number of cyberattacks is giving a wake-up call to different organizations to safeguard their businesses by using new and innovative technologies, such as SOAR, to prevent the attacks and to guard their organization’s valuable and critical data. The region's strong technology ecosystem and continuous innovation make it a key player in driving the development and adoption of these solutions globally.
Key Market Players
The security automation solution and service providers have implemented various types of organic and inorganic growth strategies, such as new product launches, product upgrades, partnerships, and agreements, business expansions, and mergers and acquisitions to strengthen their offerings in the market. Some major players in the security automation market include Palo Alto Networks (US), Splunk (US), CyberArk (US), Check Point (Israel), CrowdStrike (US), Red Hat (US), Cisco (US), Carbon Black (US), Trellix (US), IBM (US), Secureworks (US), Tenable (US), Microsoft (US), Swimlane (US), Tufin (US), Sumo Logic (US), Google (US), LogRhythm (US), Exabeam (US), ManageEngine (India), Fortinet (US), Devo Technology (US), D3 Security (Canada), Logsign (Netherlands), Vulcan Cyber (Israel), Cyware (US), Cyberbit (US), SIRP (US), Tines (Ireland), Veriti (Israel), Vanta (US), Drata (US), Anvilogic (US), and Torq (US).
Scope of the Report
|
Report Metrics |
Details |
|
Market size available for years |
2017–2028 |
|
Base year considered |
2022 |
|
Forecast period |
2023–2028 |
|
Forecast units |
USD (Billion) |
|
Segments covered |
Offering, Technology, Application, Code Type, Vertical, and Region |
|
Geographies covered |
North America, Asia Pacific, Europe, Middle East & Africa, and Latin America |
|
Companies covered |
Palo Alto Networks (US), Splunk (US), CyberArk (US), Check Point (Israel), CrowdStrike (US), Red Hat (US), Cisco (US), Carbon Black (US), Trellix (US), IBM (US), Secureworks (US), Tenable (US), Microsoft (US), Swimlane (US), Tufin (US), Sumo Logic (US), Google (US), LogRhythm (US), Exabeam (US), ManageEngine (India), Fortinet (US), Devo Technology (US), D3 Security (Canada), Logsign (Netherlands), Vulcan Cyber (Israel), Cyware (US), Cyberbit (US), SIRP (US), Tines (Ireland), Veriti (Israel), Vanta (US), Drata (US), Anvilogic (US), and Torq (US). |
This research report categorizes the security automation market based on offering, technology, application, code type, vertical, and region.
By Offering:
-
Solution
-
SOAR
- Incident Response Automation
- Case Management Automation
- Threat Intelligence Automation
- Other SOAR Solutions
-
SIEM
- Log Collection Automation
- Real-time Alerting Automation
- Incident Prioritization Automation
- Automated Incident Escalation
-
XDR
- Real-time Response Automation
- Automated Threat Hunting
- Automated Compliance Reporting
- Other XDR Solutions
-
SOAR
-
Solutions by Deployment Mode
- Cloud
- On-premise
-
Services
-
Professional Services
- Training & Consulting
- System Integration & Implementation
- Support & Maintenance
- Managed Services
-
Professional Services
By Technology:
- AI & ML
- Predictive Analytics
- RPA
- UEBA
- Other Technologies
By Application:
-
Network Security
- Intrusion Detection and Prevention Systems (IDPS)
- Firewall Management
- Network Access Control
- Network Traffic Analysis
- Others
-
Endpoint Security
- Threat Detection and Prevention
- Malware Detection and Removal
- Configuration Management
- Phishing and Email Protection
- Others
-
Incident Response Management
- Incident Triage and Escalation
- Incident categorization and prioritization
- Workflow Orchestration
- Evidence Gathering
- Others
-
Vulnerability Management
- Vulnerability Scanning and Assessment
- Prioritization
- Vulnerability Remediation and Ticketing
- Patch Management and Remediation
- Others
-
Identity and Access Management
- User Provisioning and Deprovisioning
- Single Sign-On (SSO)
- Multi-Factor Authentication (MFA)
- Access Policy Enforcement
- Others
-
Compliance and Policy Management
- Automated Compliance Auditing
- Policy Enforcement Automation
- Regulatory Compliance Reporting
- Audit Trail Generation
- Others
-
Data Protection and Encryption
- Encryption Key Management
- File and Database Encryption
- Data Loss Prevention
- Others
By Code Type:
- Low-Code
- No-Code
- Full-Code
By Vertical:
- BFSI
- Manufacturing
- Media & Entertainment
- Healthcare & Life Sciences
- Energy & Utilities
- Government & Defense
- Retail & eCommerce
- IT & ITES
- Other Verticals
By Region:
-
North America
- US
- Canada
-
Europe
- UK
- Germany
- France
- Italy
- Spain
- Rest of Europe
-
Asia Pacific
- China
- India
- Japan
- Australia and New Zealand (ANZ)
- South Korea
- ASEAN Countries
- Rest of Asia Pacific
-
Middle East & Africa
- UAE
- Saudi Arabia
- South Africa
- Israel
- Rest of the Middle East & Africa
-
Latin America
- Brazil
- Mexico
- Argentina
- Rest of Latin America
Recent Developments:
- In July 2023, Splunk and Microsoft partnered to build Splunk’s enterprise security and observability offerings on Microsoft Azure. Additionally, for the first time, Splunk solutions will be available for purchase on the Microsoft Azure Marketplace.
- In June 2023, Check Point and Everphone have announced a collaboration in advanced threat prevention for corporate smartphones. The collaboration will see Everphone enhance its DaaS solution by integrating Check Point Harmony Mobile, an industry-leading Mobile Threat Defense (MTD) solution that offers comprehensive protection against a wide range of cyber threats.
- In June 2023, Palo Alto Networks launched Cortex Xpanse Expander as a cloud-based attack surface management solution that helped organizations find and fix their known and unknown internet-connected risks. Expander performed automated, continuous scans to index the entire internet and discover all connected assets, misconfigurations, and exposed services.
- In May 2023, Vanta, a trust management platform provider, and CrowdStrike have developed an integration designed to help organizations improve their compliance and security operations. The integration builds on CrowdStrike’s investment in Vanta through the CrowdStrike Falcon Fund in September 2022.
- In April 2023, Cybersecurity company CrowdStrike announced the first visibility and threat detection solution for ChromeOS devices that does not require a mobile device management solution. CrowdStrike Falcon Insight XDR for ChromeOS delivers endpoint detection and response and extended detection and response capabilities designed to stop adversaries.
- In February 2023, Check Point has introduced Check Point Infinity Spark, a threat prevention solution that delivers industry leading AI security and integrated connectivity to small and medium-sized businesses (SMBs).
- In March 2022, CyberArk acquired Aapi.io, a provider of identity automation and orchestration solutions. This acquisition expanded CyberArk's Identity Security Platform with new capabilities for automating identity lifecycle management and privileged access management.
Frequently Asked Questions (FAQ):
What is Security Automation?
Security automation is the automation of security tasks, including both administrative duties and incident detection and response. Security automation provides numerous benefits to the organization by enabling security teams to scale to handle growing workloads. The primary goals of security automation are to enable faster incident response and to increase security agility.
What is the total CAGR expected to be recorded for the security automation market during forecast period?
The market is expected to record a CAGR of 13.4% during the forecast period.
Which are the key drivers supporting the growth of the security automation market?
Some factors driving the growth of the security automation market are rising cybersecurity threats and complexity, growing ability to detect and respond to security incidents in real-time, increasing incidents of phishing emails and ransomware, and need to ensure consistent adherence to security policies and facilitates audit trails.
Which are the key technologies prevailing in the security automation market?
The key technologies gaining a foothold in the security automation market are AI & ML, RPA, User Behaviour and Entity Behaviour Analytics (UEBA), Predictive Analytics and Others (Anomaly Detection and Behavior Analysis, Tokenization, Deception technology, and Threat Intelligence analysis).
Who are the key vendors in the security automation market?
Some major players in the security automation market include Palo Alto Networks (US), Splunk (US), CyberArk (US), Check Point (Israel), CrowdStrike (US), Red Hat (US), Cisco (US), Carbon Black (US), Trellix (US), IBM (US), Secureworks (US), Tenable (US), Microsoft (US), Swimlane (US), Tufin (US), Sumo Logic (US), Google (US), LogRhythm (US), Exabeam (US), ManageEngine (India), Fortinet (US), Devo Technology (US), D3 Security (Canada), Logsign (Netherlands), Vulcan Cyber (Israel), Cyware (US), Cyberbit (US), SIRP (US), Tines (Ireland), Veriti (Israel), Vanta (US), Drata (US), Anvilogic (US), and Torq (US).
To speak to our analyst for a discussion on the above findings, click Speak to Analyst


- 5.1 INTRODUCTION
-
5.2 MARKET DYNAMICSDRIVERS- Rise in cybersecurity threats and complexity- Increase in ability to detect and respond to security incidents in real time- Growth in incidents of phishing emails and ransomware- Need to ensure consistent adherence to security policies and facilitate audit trailsRESTRAINTS- Concerns related to data privacy- Uncertainty in third-party applicationsOPPORTUNITIES- Rise in advent of predictive analytics to anticipate potential threats- Advancements in quantum computing to mitigate quantum-based attacksCHALLENGES- Shortage of modern IT infrastructure
-
5.3 CASE STUDY ANALYSISBFSI- Superior Credit Union relied on Taegis ManagedXDR for proactive security- R3’s security team saved more than 220 hours/month with Tines- Tenable unified vulnerability management program of Global Payment AU NZ- eFinance strengthened digital payment security ecosystem in Egypt with LogRhythm SIEMHEALTHCARE- Almac Group stepped up IoT Security- McKesson chose Tines for its refreshing approach to security automation- Geisinger expanded CrowdStrike usage to protect AWS Cloud WorkloadsENERGY & UTILITIES- Bas¸kentgaz prevented potential DOS and XSS attacks by using Logsign SIEM- Botswana Power Corporation secured its infrastructure, its business, and its management's confidence with Check PointIT & ITES- Upwork used Tines to improve its security posture and help its end-users get smarter- Auth0 used Tines to deliver faster and more efficient security alert response serviceMEDIA & ENTERTAINMENT- Tines helped Canva to improve its security detection and response- The Kraft Group adopted Taegis ManagedXDR to transform its IT environmentRETAIL & ECOMMERCE- Busy Beaver took customer-first approach to IT Security- Global Retailer reduced risk with Secureworks Threat Detection And ResponseTELECOM- Vodafone Idea Limited automated to improve IT infrastructureMANUFACTURING- SMS Group maintained highest standards of security with Trellix solutionsGOVERNMENT & DEFENSE- Turkish Red Crescent used Logsign SIEM against possible cyber threatsEDUCATION- Istanbul Bilgi University observed network and system activities of users on all campuses using Logsign SIEMAUTOMOTIVE & TRANSPORTATION- Tines enabled Turo’s lean security team to do more with less
-
5.4 TARIFF AND REGULATORY LANDSCAPEREGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONSNORTH AMERICAEUROPEASIA PACIFICMIDDLE EAST & AFRICALATIN AMERICA
-
5.5 ECOSYSTEM/MARKET MAP
-
5.6 PATENT ANALYSISMETHODOLOGYPATENTS FILED, BY DOCUMENT TYPEINNOVATION AND PATENT APPLICATIONS- Top applicants
- 5.7 SUPPLY CHAIN ANALYSIS
-
5.8 FUTURE DIRECTIONS OF SECURITY AUTOMATION MARKET LANDSCAPETECHNOLOGY ROADMAP FOR SECURITY AUTOMATION MARKET UNTIL 2030
-
5.9 PRICING ANALYSISAVERAGE SELLING PRICE OF KEY COMPANIESINDICATIVE PRICING ANALYSIS
- 5.10 BRIEF HISTORY OF SECURITY AUTOMATION/EVOLUTION
- 5.11 TRENDS AND DISRUPTIONS IMPACTING BUYERS/CLIENTS’ BUSINESSES
-
5.12 PORTER’S FIVE FORCES ANALYSISTHREAT OF NEW ENTRANTSTHREAT OF SUBSTITUTESBARGAINING POWER OF SUPPLIERSBARGAINING POWER OF BUYERSINTENSITY OF COMPETITIVE RIVALRY
- 5.13 KEY CONFERENCES AND EVENTS
-
5.14 KEY STAKEHOLDERS AND BUYING CRITERIAKEY STAKEHOLDERS IN BUYING PROCESSBUYING CRITERIA
-
5.15 TECHNOLOGY ANALYSISKEY TECHNOLOGY- Artificial Intelligence and Machine Learning (AI and ML)- Biometric Authentication- Containerization and Microservices- Quantum Computing- User and Entity Behavior Analytics (UEBA)- Network Segmentation Technologies- BlockchainADJACENT TECHNOLOGY- IoT- 5G- Cloud Computing- Edge Computing- Remote Work Technologies
-
5.16 BUSINESS MODEL ANALYSISSUBSCRIPTION-BASED SERVICESFREEMIUM MODELSMANAGED SECURITY SERVICESPLATFORM AS A SERVICE (PAAS)ON-PREMISES LICENSINGUSAGE-BASED MODELSHYBRID CLOUD MODELS
-
6.1 INTRODUCTIONOFFERING: SECURITY AUTOMATION MARKET DRIVERS
-
6.2 SOLUTIONSSOAR- Incident Response Automation- Case Management Automation- Threat Intelligence Automation- Other SOAR solutionsSIEM- Log Collection Automation- Real-time Alerting Automation- Incident Prioritization Automation- Automated Incident EscalationXDR- Real-time Response Automation- Automated Threat Hunting- Automated Compliance Reporting- Other XDR solutions
-
6.3 SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODECLOUD- Cloud solutions provide scalability, allowing organizations to easily expand or contract resources based on demandON-PREMISES- On-premises solutions provide advantage of direct control over security configurations and data-handling practices
-
6.4 SERVICESPROFESSIONAL SERVICES- Training & Consulting- System Integration & Implementation- Support & MaintenanceMANAGED SERVICES
-
7.1 INTRODUCTIONTECHNOLOGY: SECURITY AUTOMATION MARKET DRIVERS
-
7.2 AI & MLGROWTH OF SECURITY AUTOMATION MARKET INTRICATELY TIED TO ADVANCEMENTS IN AI & ML TECHNOLOGIES
-
7.3 PREDICTIVE ANALYTICSPREDICTIVE ANALYTICS TO BE FORCE MULTIPLIER, ENHANCING EFFECTIVENESS OF SECURITY AUTOMATION SOLUTIONS
-
7.4 RPARPA TO EMPOWER SECURITY PROFESSIONALS TO FOCUS ON STRATEGIC INITIATIVES AND TACKLE COMPLEX CHALLENGES
-
7.5 USER BEHAVIOR & ENTITY BEHAVIOR ANALYTICS (UEBA)UEBA TO HELP ORGANIZATIONS SIGNIFICANTLY REDUCE RESPONSE TIMES AND ENHANCE OVERALL CYBERSECURITY
- 7.6 OTHER TECHNOLOGIES
-
8.1 INTRODUCTIONAPPLICATION: SECURITY AUTOMATION MARKET DRIVERS
-
8.2 NETWORK SECURITYINTRUSION DETECTION & PREVENTION SYSTEMS (IDPS)- IDPS to provide necessary monitoring and response mechanisms to meet industry standardsFIREWALL MANAGEMENT- Automation in firewall management aligned with rapid pace of modern cyber threatsNETWORK ACCESS CONTROL- Need to maintain regulatory complianceNETWORK TRAFFIC ANALYSIS- Advanced and automated approach to threat detection within network environmentsOTHER NETWORK SECURITY APPLICATIONS
-
8.3 ENDPOINT SECURITYTHREAT DETECTION & PREVENTION- Strategic advantage against relentless cyber threatsMALWARE DETECTION & REMOVAL- Demand to bridge gap between rapid evolution of threats and capabilities of human-operated security systemsCONFIGURATION MANAGEMENT- Need to reduce risk of non-compliance penalties and data breaches resulting from misconfigurationsPHISHING & EMAIL PROTECTION- Facility of automated incident response workflows to be triggered to investigate and mitigate potential threatsOTHER ENDPOINT SECURITY APPLICATIONS
-
8.4 INCIDENT RESPONSE MANAGEMENTINCIDENT CATEGORIZATION & PRIORITIZATION- Need to contribute to improved decision-making within security operationsEVIDENCE GATHERING- Automation solutions to help sift through vast amounts of data, identifying pertinent evidence while minimizing false positivesWORKFLOW ORCHESTRATION- Demand for higher consistency and accuracy in security operationsINCIDENT TRIAGE & ESCALATION- Automation to enable swift escalation of incidents to relevant teams or individuals for further investigation and responseOTHER INCIDENT RESPONSE MANAGEMENT APPLICATIONS
-
8.5 VULNERABILITY MANAGEMENTVULNERABILITY SCANNING & ASSESSMENT- Need for seamless integration into DevSecOps pipeline, identifying vulnerabilities throughout software development lifecyclePRIORITIZATION- Prioritization to aid in meeting regulatory compliance requirements by ensuring prompt addressing of most serious threatsVULNERABILITY REMEDIATION & TICKETING- Vulnerability remediation to significantly reduce organizations’ exposure to potential breaches, minimizing impact of cyber threatsPATCH MANAGEMENT & REMEDIATION- Packet management & remediation: An indispensable component of robust cybersecurity strategyOTHER VULNERABILITY MANAGEMENT APPLICATIONS
-
8.6 IDENTITY & ACCESS MANAGEMENT (IAM)USER PROVISIONING & DEPROVISIONING- Organizations’ need to stay compliant by providing auditable trail of access changesMULTI-FACTOR AUTHENTICATION (MFA)- Need to strengthen organizations’ defenses against various threats, including phishing attacks and credential theftSINGLE SIGN-ON (SSO)- SSO to minimize potential attack surface and reduce likelihood of password-related security incidentsACCESS POLICY ENFORCEMENT- Access policy enforcement to address escalating challenge of managing access rights in complex and dynamic IT environmentsOTHER IDENTITY & ACCESS MANAGEMENT APPLICATIONS
-
8.7 COMPLIANCE & POLICY MANAGEMENTAUTOMATED COMPLIANCE AUDITING- Automated auditing to help organizations proactively identify and rectify compliance gaps before serious repercussionsPOLICY ENFORCEMENT AUTOMATION- Policy enforcement automation to gain traction due to its ability to enhance both efficiency and effectivenessREGULATORY COMPLIANCE REPORTING- Proactive monitoring and alerting to help organizations identify potential compliance breaches early on and take corrective actionsAUDIT TRAIL GENERATION- Automation to generate audit trails, ensuring accuracy, consistency, and timely reportingOTHER COMPLIANCE & POLICY MANAGEMENT APPLICATIONS
-
8.8 DATA PROTECTION & ENCRYPTIONENCRYPTION KEY MANAGEMENT- Integration into broader security automation strategies to enhance data protection, reduce operational overhead, and ensure regulatory complianceFILE & DATABASE ENCRYPTION- File and database encryption to enhance data security while maintaining operational efficiencyDATA LOSS PREVENTION- DLP solutions to aid in identify patterns, anomalies, and potential risks across these data flows in real timeOTHER DATA PROTECTION & ENCRYPTION APPLICATIONS
-
8.9 OTHER APPLICATIONSCYBER THREAT INTELLIGENCE- Security automation to enable real-time threat hunting and incident responseTHREAT FEED INTEGRATION- Threat feed integration to align with shift from reactive to proactive cybersecurity practicesEVENT-TRIGGERED AUTOMATION- Event-triggered automation to minimize impact of cyber incidents with optimizing resource allocation
-
9.1 INTRODUCTIONCODE TYPE: SECURITY AUTOMATION SOFTWARE MARKET DRIVERS
-
9.2 LOW-CODELOW-CODE PLATFORMS PROVIDE ORGANIZATIONS WITH AGILITY NEEDED TO COUNTER EVER-EVOLVING LANDSCAPE OF CYBER THREATS
-
9.3 NO-CODENO-CODE SOFTWARE OFFERS DEMOCRATIZED APPROACH TO BUILDING AND IMPLEMENTING SECURITY AUTOMATION SOLUTIONS
-
9.4 FULL-CODEABILITY TO MINIMIZE HUMAN ERROR, ACCELERATE DEVELOPMENT CYCLES, AND ENHANCE SECURITY MEASURES
-
10.1 INTRODUCTIONVERTICAL: SECURITY AUTOMATION MARKET DRIVERSMAJOR USE CASES, BY VERTICAL
- 10.2 BANKING, FINANCIAL SERVICES, AND INSURANCE
- 10.3 MEDIA & ENTERTAINMENT
- 10.4 MANUFACTURING
- 10.5 GOVERNMENT & DEFENSE
- 10.6 ENERGY & UTILITIES
- 10.7 RETAIL & ECOMMERCE
- 10.8 HEALTHCARE & LIFE SCIENCES
- 10.9 IT & ITES
- 10.10 OTHER VERTICALS
- 11.1 INTRODUCTION
-
11.2 NORTH AMERICANORTH AMERICA: SECURITY AUTOMATION MARKET DRIVERSNORTH AMERICA: RECESSION IMPACTUS- Advanced technologies to increase security risks and threats to be addressedCANADA- Private sector participation to play crucial role in advancement of security automation technology
-
11.3 EUROPEEUROPE: SECURITY AUTOMATION MARKET DRIVERSEUROPE: RECESSION IMPACTUK- Demand to strengthen cybersecurity posture by embracing automation and advanced technologiesGERMANY- German government emphasized regulatory frameworks and standards to encourage adoption of security automation technologyFRANCE- France leverages AI & ML to strengthen its cybersecurity defensesSPAIN- Spanish organizations look to improve security posture and reduce risk of cyberattacksITALY- National cybersecurity strategy includes plans pertaining to R&DREST OF EUROPE
-
11.4 ASIA PACIFICASIA PACIFIC: SECURITY AUTOMATION MARKET DRIVERSASIA PACIFIC: RECESSION IMPACTCHINA- China emerged proactive in leveraging AI and automation to bolster its cybersecurity capabilitiesJAPAN- Integrating automation into its cybersecurity framework highlighted Japan’s commitment to addressing evolving cyber threatsINDIA- India focuses on collaborations, innovation hubs, policy initiatives, and talent developmentSOUTH KOREA- Significant strides in AI research, development, and deployment and focus of companies on developing AI devicesAUSTRALIA & NEW ZEALAND- Australia & New Zealand actively embrace security automation as cornerstone of their cybersecurity strategiesASEAN COUNTRIES- ASEAN countries’ notable surge in adoption of security automation reflects region’s commitment to enhancing cybersecurity and safeguarding digital assetsREST OF ASIA PACIFIC
-
11.5 MIDDLE EAST & AFRICAMIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET DRIVERSMIDDLE EAST & AFRICA: RECESSION IMPACTUAE- Strategic deployment of AI and advanced technologies across various sectorsSAUDI ARABIA- Government’s strong commitment toward advancing security automation initiativesSOUTH AFRICA- Investment in advanced security automation solutions by several South African organizations to bolster incident response capabilitiesISRAEL- Surge in startups specializing in AI-driven threat detection, autonomous incident response, and predictive analyticsREST OF MIDDLE EAST & AFRICA
-
11.6 LATIN AMERICALATIN AMERICA: SECURITY AUTOMATION MARKET DRIVERSLATIN AMERICA: RECESSION IMPACTBRAZIL- Proactive approach to adopting security automation technologyMEXICO- Investment in initiatives to foster R&D in AI-driven cybersecurity technologiesARGENTINA- Argentina to witness high growth as organizations seek to improve threat detection, incident response, and overall security managementREST OF LATIN AMERICA

- 12.1 OVERVIEW
- 12.2 STRATEGIES ADOPTED BY KEY PLAYERS
-
12.3 REVENUE ANALYSISBUSINESS SEGMENT REVENUE ANALYSIS
- 12.4 MARKET SHARE ANALYSIS
-
12.5 COMPANY EVALUATION MATRIXSTARSEMERGING LEADERSPERVASIVE PLAYERSPARTICIPANTSCOMPANY PRODUCT FOOTPRINT
-
12.6 STARTUP/SME EVALUATION MATRIXPROGRESSIVE COMPANIESRESPONSIVE COMPANIESDYNAMIC COMPANIESSTARTING BLOCKSSTARTUP/SME COMPETITIVE BENCHMARKING
-
12.7 BRAND/PRODUCT COMPARATIVE ANALYSIS IN SECURITY AUTOMATION MARKETCOMPARATIVE ANALYSIS OF SECURITY AUTOMATION PRODUCTS
- 12.8 VALUATION AND FINANCIAL METRICS OF KEY SECURITY AUTOMATION VENDORS
-
12.9 COMPETITIVE SCENARIO AND TRENDSPRODUCT LAUNCHES AND ENHANCEMENTSDEALS
- 13.1 INTRODUCTION
-
13.2 KEY PLAYERSPALO ALTO NETWORKS- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewSPLUNK- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewCYBERARK- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewCHECK POINT- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewCROWDSTRIKE- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewRED HAT- Business overview- Products/Solutions/Services offered- Recent developmentsCISCO- Business overview- Products/Solutions/Services offered- Recent developmentsCARBON BLACK- Business overview- Products/Solutions/Services offered- Recent developmentsTRELLIX- Business overview- Products/Solutions/Services offered- Recent developmentsIBM- Business overview- Products/Solutions/Services offered- Recent developmentsSECUREWORKS- Business overview- Products/Solutions/Services offered- Recent developmentsTENABLE- Business overview- Products/Solutions/Services offered- Recent developments
-
13.3 OTHER KEY PLAYERSMICROSOFTSWIMLANETUFINSUMO LOGICGOOGLELOGRHYTHMEXABEAMMANAGEENGINEFORTINETDEVO TECHNOLOGYD3 SECURITYLOGSIGN
-
13.4 STARTUP/SME PROFILESVULCAN CYBERCYWARECYBERBITSIRPTINESVERITIVANTADRATAANVILOGICTORQ
- 14.1 INTRODUCTION
-
14.2 SECURITY ORCHESTRATION, AUTOMATION, AND RESPONSE (SOAR) MARKET - GLOBAL FORECAST TO 2027MARKET DEFINITIONMARKET OVERVIEW- SOAR market, by offering- SOAR market, by application- SOAR market, by organization size- SOAR market, by vertical- SOAR market, by region
-
14.3 SECURITY ANALYTICS MARKET - GLOBAL FORECAST TO 2026MARKET DEFINITIONMARKET OVERVIEW- Security analytics market, by application- Security analytics market, by component- Security analytics market, by deployment mode- Security analytics market, by organization size- Security analytics market, by industry vertical- Security analytics market, by region
- 15.1 DISCUSSION GUIDE
- 15.2 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
- 15.3 CUSTOMIZATION OPTIONS
- 15.4 RELATED REPORTS
- 15.5 AUTHOR DETAILS
- TABLE 1 FACTOR ANALYSIS
- TABLE 2 IMPACT OF RECESSION ON GLOBAL SECURITY AUTOMATION MARKET
- TABLE 3 SECURITY AUTOMATION MARKET SIZE AND GROWTH RATE, 2017–2022 (USD MILLION, Y-O-Y GROWTH)
- TABLE 4 SECURITY AUTOMATION MARKET SIZE AND GROWTH RATE, 2023–2028 (USD MILLION, Y-O-Y GROWTH)
- TABLE 5 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 6 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 7 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 8 MIDDLE EAST & AFRICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 9 LATIN AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 10 SECURITY AUTOMATION MARKET: SUPPLY CHAIN ANALYSIS
- TABLE 11 PATENTS FILED, 2013–2023
- TABLE 12 TOP 20 PATENT OWNERS IN SECURITY AUTOMATION MARKET, 2013–2023
- TABLE 13 LIST OF PATENTS IN SECURITY AUTOMATION MARKET, 2023
- TABLE 14 AVERAGE SELLING PRICE ANALYSIS, BY OFFERING
- TABLE 15 DETAILED LIST OF CONFERENCES AND EVENTS, 2023–2024
- TABLE 16 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE APPLICATIONS
- TABLE 17 KEY BUYING CRITERIA FOR TOP THREE APPLICATIONS
- TABLE 18 SECURITY AUTOMATION MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 19 SECURITY AUTOMATION MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 20 SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 21 SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 22 SOAR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 23 SOAR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 24 SOAR SOLUTIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 25 SOAR SOLUTIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 26 INCIDENT RESPONSE AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 27 INCIDENT RESPONSE AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 28 CASE MANAGEMENT AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 29 CASE MANAGEMENT AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 30 THREAT INTELLIGENCE AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 31 THREAT INTELLIGENCE AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 32 OTHER SOAR SOLUTIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 33 OTHER SOAR SOLUTIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 34 SIEM SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 35 SIEM SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 36 SIEM SOLUTIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 37 SIEM SOLUTIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 38 LOG COLLECTION AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 39 LOG COLLECTION AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 40 REAL-TIME ALERTING AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 41 REAL-TIME ALERTING AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 42 INCIDENT PRIORITIZATION AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 43 INCIDENT PRIORITIZATION AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 44 AUTOMATED INCIDENT ESCALATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 45 AUTOMATED INCIDENT ESCALATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 46 XDR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 47 XDR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 48 XDR SOLUTIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 49 XDR SOLUTIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 50 REAL-TIME RESPONSE AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 51 REAL-TIME RESPONSE AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 52 AUTOMATED THREAT HUNTING MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 53 AUTOMATED THREAT HUNTING MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 54 AUTOMATED COMPLIANCE REPORTING MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 55 AUTOMATED COMPLIANCE REPORTING MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 56 OTHER XDR SOLUTIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 57 OTHER XDR SOLUTIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 58 SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 59 SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 60 CLOUD-BASED SECURITY AUTOMATION SOLUTIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 61 CLOUD-BASED SECURITY AUTOMATION SOLUTIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 62 ON-PREMISE SECURITY AUTOMATION SOLUTIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 63 ON-PREMISE SECURITY AUTOMATION SOLUTIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 64 SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 65 SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 66 SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 67 SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 68 SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 69 SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 70 SECURITY AUTOMATION TRAINING & CONSULTING SERVICES MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 71 SECURITY AUTOMATION TRAINING & CONSULTING SERVICES, BY REGION, 2023–2028 (USD MILLION)
- TABLE 72 SECURITY AUTOMATION SYSTEM INTEGRATION & IMPLEMENTATION SERVICES MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 73 SECURITY AUTOMATION SYSTEM INTEGRATION & IMPLEMENTATION SERVICES MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 74 SECURITY AUTOMATION SUPPORT & MAINTENANCE SERVICES MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 75 SECURITY AUTOMATION SUPPORT & MAINTENANCE SERVICES MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 76 SECURITY AUTOMATION MANAGED SERVICES MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 77 SECURITY AUTOMATION MANAGED SERVICES MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 78 SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2017–2022 (USD MILLION)
- TABLE 79 SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2023–2028 (USD MILLION)
- TABLE 80 AI & ML IN SECURITY AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 81 AI & ML IN SECURITY AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 82 PREDICTIVE ANALYTICS IN SECURITY AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 83 PREDICTIVE ANALYTICS IN SECURITY AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 84 RPA IN SECURITY AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 85 RPA IN SECURITY AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 86 UEBA IN SECURITY AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 87 UEBA IN SECURITY AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 88 OTHER TECHNOLOGIES IN SECURITY AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 89 OTHER TECHNOLOGIES IN SECURITY AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 90 SECURITY AUTOMATION MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 91 SECURITY AUTOMATION MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 92 NETWORK SECURITY APPLICATIONS MARKET, BY SUBAPPLICATION, 2017–2022 (USD MILLION)
- TABLE 93 NETWORK SECURITY APPLICATIONS MARKET, BY SUBAPPLICATION, 2023–2028 (USD MILLION)
- TABLE 94 NETWORK SECURITY APPLICATIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 95 NETWORK SECURITY APPLICATIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 96 ENDPOINT SECURITY APPLICATIONS MARKET, BY SUBAPPLICATION, 2017–2022 (USD MILLION)
- TABLE 97 ENDPOINT SECURITY APPLICATIONS MARKET, BY SUBAPPLICATION, 2023–2028 (USD MILLION)
- TABLE 98 ENDPOINT SECURITY APPLICATIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 99 ENDPOINT SECURITY APPLICATIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 100 INCIDENT RESPONSE MANAGEMENT APPLICATIONS MARKET, BY SUBAPPLICATION, 2017–2022 (USD MILLION)
- TABLE 101 INCIDENT RESPONSE MANAGEMENT APPLICATIONS MARKET, BY SUBAPPLICATION, 2023–2028 (USD MILLION)
- TABLE 102 INCIDENT RESPONSE MANAGEMENT APPLICATIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 103 INCIDENT RESPONSE MANAGEMENT APPLICATIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 104 VULNERABILITY MANAGEMENT APPLICATIONS MARKET, BY SUBAPPLICATION, 2017–2022 (USD MILLION)
- TABLE 105 VULNERABILITY MANAGEMENT APPLICATIONS MARKET, BY SUBAPPLICATION, 2023–2028 (USD MILLION)
- TABLE 106 VULNERABILITY MANAGEMENT APPLICATIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 107 VULNERABILITY MANAGEMENT APPLICATIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 108 IDENTITY & ACCESS MANAGEMENT APPLICATIONS MARKET, BY SUBAPPLICATION, 2017–2022 (USD MILLION)
- TABLE 109 IDENTITY & ACCESS MANAGEMENT APPLICATIONS MARKET, BY SUBAPPLICATION, 2023–2028 (USD MILLION)
- TABLE 110 IDENTITY & ACCESS MANAGEMENT APPLICATIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 111 IDENTITY & ACCESS MANAGEMENT APPLICATIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 112 COMPLIANCE & POLICY MANAGEMENT APPLICATIONS MARKET, BY SUBAPPLICATION, 2017–2022 (USD MILLION)
- TABLE 113 COMPLIANCE & POLICY MANAGEMENT APPLICATIONS MARKET, BY SUBAPPLICATION, 2023–2028 (USD MILLION)
- TABLE 114 COMPLIANCE & POLICY MANAGEMENT APPLICATIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 115 COMPLIANCE & POLICY MANAGEMENT APPLICATIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 116 DATA PROTECTION & ENCRYPTION APPLICATIONS MARKET, BY SUBAPPLICATION, 2017–2022 (USD MILLION)
- TABLE 117 DATA PROTECTION & ENCRYPTION APPLICATIONS MARKET, BY SUBAPPLICATION, 2023–2028 (USD MILLION)
- TABLE 118 DATA PROTECTION & ENCRYPTION APPLICATIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 119 DATA PROTECTION & ENCRYPTION APPLICATIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 120 OTHER APPLICATIONS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 121 OTHER APPLICATIONS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 122 SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2017–2022 (USD MILLION)
- TABLE 123 SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2023–2028 (USD MILLION)
- TABLE 124 LOW-CODE SECURITY AUTOMATION SOFTWARE MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 125 LOW-CODE SECURITY AUTOMATION SOFTWARE MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 126 NO-CODE SECURITY AUTOMATION SOFTWARE MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 127 NO-CODE SECURITY AUTOMATION SOFTWARE MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 128 FULL-CODE SECURITY AUTOMATION SOFTWARE MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 129 FULL-CODE SECURITY AUTOMATION SOFTWARE MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 130 SECURITY AUTOMATION MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 131 SECURITY AUTOMATION MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 132 BANKING, FINANCIAL SERVICES, AND INSURANCE VERTICAL MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 133 BANKING, FINANCIAL SERVICES, AND INSURANCE VERTICAL MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 134 MEDIA & ENTERTAINMENT VERTICAL MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 135 MEDIA & ENTERTAINMENT VERTICAL MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 136 MANUFACTURING VERTICAL MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 137 MANUFACTURING VERTICAL MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 138 GOVERNMENT & DEFENSE VERTICAL MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 139 GOVERNMENT & DEFENSE VERTICAL MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 140 ENERGY & UTILITIES VERTICAL MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 141 ENERGY & UTILITIES VERTICAL MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 142 RETAIL & ECOMMERCE VERTICAL MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 143 RETAIL & ECOMMERCE VERTICAL MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 144 HEALTHCARE & LIFE SCIENCES VERTICAL MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 145 HEALTHCARE & LIFE SCIENCES VERTICAL MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 146 IT & ITES VERTICAL MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 147 IT & ITES VERTICAL MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 148 OTHER VERTICALS MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 149 OTHER VERTICALS MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 150 SECURITY AUTOMATION MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 151 SECURITY AUTOMATION MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 152 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 153 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 154 NORTH AMERICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 155 NORTH AMERICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 156 NORTH AMERICA: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 157 NORTH AMERICA: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 158 NORTH AMERICA: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 159 NORTH AMERICA: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 160 NORTH AMERICA: SOAR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 161 NORTH AMERICA: SOAR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 162 NORTH AMERICA: SIEM SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 163 NORTH AMERICA: SIEM SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 164 NORTH AMERICA: XDR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 165 NORTH AMERICA: XDR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 166 NORTH AMERICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 167 NORTH AMERICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 168 NORTH AMERICA: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2017–2022 (USD MILLION)
- TABLE 169 NORTH AMERICA: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2023–2028 (USD MILLION)
- TABLE 170 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2017–2022 (USD MILLION)
- TABLE 171 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2023–2028 (USD MILLION)
- TABLE 172 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 173 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 174 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 175 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 176 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 177 NORTH AMERICA: SECURITY AUTOMATION MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 178 EUROPE: SECURITY AUTOMATION MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 179 EUROPE: SECURITY AUTOMATION MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 180 EUROPE: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 181 EUROPE: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 182 EUROPE: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 183 EUROPE: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 184 EUROPE: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 185 EUROPE: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 186 EUROPE: SOAR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 187 EUROPE: SOAR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 188 EUROPE: SIEM SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 189 EUROPE: SIEM SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 190 EUROPE: XDR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 191 EUROPE: XDR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 192 EUROPE: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 193 EUROPE: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 194 EUROPE: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2017–2022 (USD MILLION)
- TABLE 195 EUROPE: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2023–2028 (USD MILLION)
- TABLE 196 EUROPE: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2017–2022 (USD MILLION)
- TABLE 197 EUROPE: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2023–2028 (USD MILLION)
- TABLE 198 EUROPE: SECURITY AUTOMATION MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 199 EUROPE: SECURITY AUTOMATION MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 200 EUROPE: SECURITY AUTOMATION MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 201 EUROPE: SECURITY AUTOMATION MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 202 EUROPE: SECURITY AUTOMATION MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 203 EUROPE: SECURITY AUTOMATION MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 204 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 205 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 206 ASIA PACIFIC: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 207 ASIA PACIFIC: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 208 ASIA PACIFIC: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 209 ASIA PACIFIC: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 210 ASIA PACIFIC: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 211 ASIA PACIFIC: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 212 ASIA PACIFIC: SOAR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 213 ASIA PACIFIC: SOAR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 214 ASIA PACIFIC: SIEM SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 215 ASIA PACIFIC: SIEM SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 216 ASIA PACIFIC: XDR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 217 ASIA PACIFIC: XDR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 218 ASIA PACIFIC: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 219 ASIA PACIFIC: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 220 ASIA PACIFIC: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2017–2022 (USD MILLION)
- TABLE 221 ASIA PACIFIC: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2023–2028 (USD MILLION)
- TABLE 222 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2017–2022 (USD MILLION)
- TABLE 223 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2023–2028 (USD MILLION)
- TABLE 224 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 225 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 226 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 227 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 228 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY COUNTRY/REGION, 2017–2022 (USD MILLION)
- TABLE 229 ASIA PACIFIC: SECURITY AUTOMATION MARKET, BY COUNTRY/REGION, 2023–2028 (USD MILLION)
- TABLE 230 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 231 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 232 MIDDLE EAST & AFRICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 233 MIDDLE EAST & AFRICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 234 MIDDLE EAST & AFRICA: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 235 MIDDLE EAST & AFRICA: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 236 MIDDLE EAST & AFRICA: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 237 MIDDLE EAST & AFRICA: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 238 MIDDLE EAST & AFRICA: SOAR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 239 MIDDLE EAST & AFRICA: SOAR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 240 MIDDLE EAST & AFRICA: SIEM SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 241 MIDDLE EAST & AFRICA: SIEM SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 242 MIDDLE EAST & AFRICA: XDR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 243 MIDDLE EAST & AFRICA: XDR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 244 MIDDLE EAST & AFRICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 245 MIDDLE EAST & AFRICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 246 MIDDLE EAST & AFRICA: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2017–2022 (USD MILLION)
- TABLE 247 MIDDLE EAST & AFRICA: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2023–2028 (USD MILLION)
- TABLE 248 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2017–2022 (USD MILLION)
- TABLE 249 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2023–2028 (USD MILLION)
- TABLE 250 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 251 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 252 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 253 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 254 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 255 MIDDLE EAST & AFRICA: SECURITY AUTOMATION MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 256 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 257 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 258 LATIN AMERICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 259 LATIN AMERICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 260 LATIN AMERICA: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 261 LATIN AMERICA: SECURITY AUTOMATION SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 262 LATIN AMERICA: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 263 LATIN AMERICA: SECURITY AUTOMATION PROFESSIONAL SERVICES MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 264 LATIN AMERICA: SOAR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 265 LATIN AMERICA: SOAR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 266 LATIN AMERICA: SIEM SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 267 LATIN AMERICA: SIEM SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 268 LATIN AMERICA: XDR SOLUTIONS MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 269 LATIN AMERICA: XDR SOLUTIONS MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 270 LATIN AMERICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 271 LATIN AMERICA: SECURITY AUTOMATION SOLUTIONS MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 272 LATIN AMERICA: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2017–2022 (USD MILLION)
- TABLE 273 LATIN AMERICA: SECURITY AUTOMATION SOFTWARE MARKET, BY CODE TYPE, 2023–2028 (USD MILLION)
- TABLE 274 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2017–2022 (USD MILLION)
- TABLE 275 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY TECHNOLOGY, 2023–2028 (USD MILLION)
- TABLE 276 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 277 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 278 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 279 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 280 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 281 LATIN AMERICA: SECURITY AUTOMATION MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 282 OVERVIEW OF STRATEGIES ADOPTED BY KEY SECURITY AUTOMATION VENDORS
- TABLE 283 SECURITY AUTOMATION MARKET: DEGREE OF COMPETITION
- TABLE 284 OVERALL PRODUCT FOOTPRINT ANALYSIS (KEY PLAYERS), 2022
- TABLE 285 OVERALL PRODUCT FOOTPRINT ANALYSIS (OTHER KEY PLAYERS), 2022
- TABLE 286 DETAILED LIST OF KEY STARTUPS/SMES
- TABLE 287 PRODUCT FOOTPRINT ANALYSIS OF STARTUPS/SMES, 2022
- TABLE 288 COMPARATIVE ANALYSIS OF TRENDING SECURITY AUTOMATION PRODUCTS
- TABLE 289 COMPARATIVE ANALYSIS OF OTHER SECURITY AUTOMATION PRODUCTS
- TABLE 290 NEW PRODUCT LAUNCHES AND ENHANCEMENTS, 2022–2023
- TABLE 291 DEALS, 2021–2023
- TABLE 292 PALO ALTO NETWORKS: BUSINESS OVERVIEW
- TABLE 293 PALO ALTO NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 294 PALO ALTO NETWORKS: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 295 PALO ALTO NETWORKS: DEALS
- TABLE 296 SPLUNK: BUSINESS OVERVIEW
- TABLE 297 SPLUNK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 298 SPLUNK: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 299 SPLUNK: DEALS
- TABLE 300 CYBERARK: BUSINESS OVERVIEW
- TABLE 301 CYBERARK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 302 CYBERARK: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 303 CYBERARK: DEALS
- TABLE 304 CHECK POINT: BUSINESS OVERVIEW
- TABLE 305 CHECK POINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 306 CHECK POINT: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 307 CHECK POINT: DEALS
- TABLE 308 CROWDSTRIKE: BUSINESS OVERVIEW
- TABLE 309 CROWDSTRIKE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 310 CROWDSTRIKE: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 311 CROWDSTRIKE: DEALS
- TABLE 312 RED HAT: BUSINESS OVERVIEW
- TABLE 313 RED HAT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 314 RED HAT: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 315 RED HAT: DEALS
- TABLE 316 CISCO: BUSINESS OVERVIEW
- TABLE 317 CISCO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 318 CISCO: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 319 CISCO: DEALS
- TABLE 320 CARBON BLACK: BUSINESS OVERVIEW
- TABLE 321 CARBON BLACK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 322 CARBON BLACK: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 323 TRELLIX: BUSINESS OVERVIEW
- TABLE 324 TRELLIX: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 325 TRELLIX: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 326 TRELLIX: DEALS
- TABLE 327 IBM: BUSINESS OVERVIEW
- TABLE 328 IBM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 329 IBM: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 330 IBM: DEALS
- TABLE 331 SECUREWORKS: BUSINESS OVERVIEW
- TABLE 332 SECUREWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 333 SECUREWORKS: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 334 TENABLE: BUSINESS OVERVIEW
- TABLE 335 TENABLE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 336 TENABLE: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 337 TENABLE: DEALS
- TABLE 338 SOAR MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 339 SOAR MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 340 SOAR MARKET, BY DATA SOURCE, 2018–2021 (USD MILLION)
- TABLE 341 SOAR MARKET, BY DATA SOURCE, 2022–2027 (USD MILLION)
- TABLE 342 SOAR MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 343 SOAR MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 344 SOAR MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
- TABLE 345 SOAR MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 346 SOAR MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 347 SOAR MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 348 SECURITY ANALYTICS MARKET SIZE, BY APPLICATION, 2015–2020 (USD MILLION)
- TABLE 349 SECURITY ANALYTICS MARKET SIZE, BY APPLICATION, 2021–2026 (USD MILLION)
- TABLE 350 SECURITY ANALYTICS MARKET SIZE, BY COMPONENT, 2015–2020 (USD MILLION)
- TABLE 351 SECURITY ANALYTICS MARKET SIZE, BY COMPONENT, 2021–2026 (USD MILLION)
- TABLE 352 SECURITY ANALYTICS MARKET SIZE, BY DEPLOYMENT MODE, 2015–2020 (USD MILLION)
- TABLE 353 SECURITY ANALYTICS MARKET SIZE, BY DEPLOYMENT MODE, 2021–2026 (USD MILLION)
- TABLE 354 SECURITY ANALYTICS MARKET SIZE, BY ORGANIZATION SIZE, 2015–2020 (USD MILLION)
- TABLE 355 SECURITY ANALYTICS MARKET SIZE, BY ORGANIZATION SIZE, 2021–2026 (USD MILLION)
- TABLE 356 SECURITY ANALYTICS MARKET SIZE, BY VERTICAL, 2015–2020 (USD MILLION)
- TABLE 357 SECURITY ANALYTICS MARKET SIZE, BY VERTICAL, 2021–2026 (USD MILLION)
- TABLE 358 SECURITY ANALYTICS MARKET SIZE, BY REGION, 2015–2020 (USD MILLION)
- TABLE 359 SECURITY ANALYTICS MARKET SIZE, BY REGION, 2021–2026 (USD MILLION)
- FIGURE 1 SECURITY AUTOMATION MARKET: RESEARCH DESIGN
- FIGURE 2 DATA TRIANGULATION
- FIGURE 3 SECURITY AUTOMATION MARKET: TOP-DOWN AND BOTTOM-UP APPROACHES
- FIGURE 4 APPROACH 1 (SUPPLY-SIDE): REVENUE FROM SOLUTIONS/SERVICES OF SECURITY AUTOMATION MARKET
- FIGURE 5 APPROACH 2 (BOTTOM-UP, SUPPLY-SIDE): COLLECTIVE REVENUE FROM ALL SECURITY AUTOMATION SOLUTION/SERVICE VENDORS
- FIGURE 6 APPROACH 3 (BOTTOM-UP, SUPPLY-SIDE): FLOWCHART OF ESTIMATION AND SOURCES
- FIGURE 7 APPROACH 4 (BOTTOM-UP, DEMAND-SIDE): SHARE OF SECURITY AUTOMATION THROUGH OVERALL SECURITY AUTOMATION SPENDING
- FIGURE 8 SECURITY AUTOMATION SOLUTIONS TO LEAD OVER SERVICES MARKET IN 2023
- FIGURE 9 SOAR SOLUTIONS TO ACCOUNT FOR LARGEST MARKET SHARE IN 2023
- FIGURE 10 THREAT INTELLIGENCE AUTOMATION TO LEAD SOAR SOLUTIONS MARKET IN 2023
- FIGURE 11 REAL-TIME ALERTING AUTOMATION TO LEAD SIEM SOLUTIONS MARKET IN 2023
- FIGURE 12 REAL-TIME RESPONSE AUTOMATION TO BE LARGEST XDR SOLUTIONS MARKET IN 2023
- FIGURE 13 PROFESSIONAL SERVICES SEGMENT TO LEAD OVER MANAGED SERVICES IN 2023
- FIGURE 14 SYSTEM INTEGRATION & IMPLEMENTATION TO BE LARGEST PROFESSIONAL SERVICES MARKET IN 2023
- FIGURE 15 LOW-CODE SECURITY AUTOMATION TO BE LARGEST CODE TYPE MARKET IN 2023
- FIGURE 16 AI & ML TECHNOLOGY TO LEAD MARKET IN 2023
- FIGURE 17 NETWORK SECURITY TO BE LARGEST APPLICATION MARKET IN 2023
- FIGURE 18 FIREWALL MANAGEMENT TO BE LARGEST NETWORK SECURITY APPLICATION MARKET IN 2023
- FIGURE 19 THREAT DETECTION & PREVENTION TO BE LARGEST ENDPOINT SECURITY APPLICATION MARKET IN 2023
- FIGURE 20 INCIDENT TRIAGE & ESCALATION TO BE LARGEST INCIDENT RESPONSE MANAGEMENT APPLICATION MARKET IN 2023
- FIGURE 21 VULNERABILITY SCANNING & ASSESSMENT TO BE LARGEST VULNERABILITY MANAGEMENT APPLICATION MARKET IN 2023
- FIGURE 22 USER PROVISIONING & DEPROVISIONING TO BE LARGEST IAM APPLICATION MARKET IN 2023
- FIGURE 23 AUTOMATED COMPLIANCE AUDITING TO BE LARGEST COMPLIANCE & POLICY MANAGEMENT APPLICATION MARKET IN 2023
- FIGURE 24 ENCRYPTION KEY MANAGEMENT TO LEAD LARGEST DATA PROTECTION & ENCRYPTION MANAGEMENT APPLICATION MARKET IN 2023
- FIGURE 25 CLOUD SEGMENT ESTIMATED TO ACCOUNT FOR LARGER MARKET IN 2023
- FIGURE 26 HEALTHCARE & LIFE SCIENCES SEGMENT TO GROW AT HIGHEST CAGR IN 2023
- FIGURE 27 NORTH AMERICA TO ACCOUNT FOR LARGEST MARKET SHARE; ASIA PACIFIC TO GROW AT HIGHEST CAGR
- FIGURE 28 INCREASE IN PHISHING EMAILS AND RANSOMWARE INCIDENTS TO FACILITATE AUDIT TRAILS TO DRIVE MARKET GROWTH
- FIGURE 29 SECURITY AUTOMATION MARKET TO WITNESS MINOR DECLINE IN Y-O-Y GROWTH IN 2023
- FIGURE 30 IDENTITY & ACCESS MANAGEMENT SEGMENT TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 31 SOLUTION OFFERINGS AND BFSI VERTICAL TO ACCOUNT FOR LARGEST RESPECTIVE MARKET SHARES IN NORTH AMERICA IN 2023
- FIGURE 32 NORTH AMERICA TO ACCOUNT FOR LARGEST MARKET SHARE IN 2023
- FIGURE 33 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES: SECURITY AUTOMATION MARKET
- FIGURE 34 SECURITY AUTOMATION MARKET ECOSYSTEM
- FIGURE 35 TOTAL NUMBER OF PATENTS GRANTED, 2013–2023
- FIGURE 36 TOP TEN PATENT APPLICANT COMPANIES, 2013–2023
- FIGURE 37 REGIONAL ANALYSIS OF PATENTS GRANTED FOR SECURITY AUTOMATION MARKET, 2023
- FIGURE 38 SECURITY AUTOMATION MARKET: SUPPLY CHAIN ANALYSIS
- FIGURE 39 SECURITY AUTOMATION ROADMAP UNTIL 2030
- FIGURE 40 AVERAGE SELLING PRICE OF KEY COMPANIES
- FIGURE 41 SECURITY AUTOMATION MARKET EVOLUTION
- FIGURE 42 TRENDS AND DISRUPTIONS IMPACTING BUYERS/CLIENTS’ BUSINESSES
- FIGURE 43 PORTER’S FIVE FORCES ANALYSIS
- FIGURE 44 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE APPLICATIONS
- FIGURE 45 KEY BUYING CRITERIA FOR TOP THREE APPLICATIONS
- FIGURE 46 SECURITY AUTOMATION SERVICES TO REGISTER HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 47 XDR SOLUTIONS TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 48 THREAT INTELLIGENCE AUTOMATION TO GROW AT HIGHEST CAGR AMONG SOAR SOLUTIONS DURING FORECAST PERIOD
- FIGURE 49 REAL-TIME ALERTING AUTOMATION TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 50 AUTOMATED THREAT HUNTING SOLUTIONS TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 51 CLOUD DEPLOYMENT OF SECURITY AUTOMATION SOLUTIONS TO GROW AT HIGHER CAGR THAN ON-PREMISE SOLUTIONS
- FIGURE 52 MANAGED SERVICES TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 53 TRAINING & CONSULTING SERVICES TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 54 PREDICTIVE ANALYTICS TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 55 IDENTITY & ACCESS MANAGEMENT APPLICATION TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 56 NETWORK ACCESS CONTROL APPLICATION TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 57 MALWARE DETECTION & REMOVAL APPLICATION TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 58 INCIDENT CATEGORIZATION & PRIORITIZATION APPLICATION TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 59 PRIORITIZATION APPLICATION TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 60 SINGLE SIGN-ON APPLICATION TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 61 POLICY ENFORCEMENT AUTOMATION APPLICATION TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 62 FILE & DATABASE ENCRYPTION APPLICATION TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 63 LOW-CODE SEGMENT TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 64 HEALTHCARE & LIFE SCIENCES VERTICAL TO WITNESS HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 65 ASIA PACIFIC TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 66 INDIA TO WITNESS HIGHEST GROWTH DURING FORECAST PERIOD
- FIGURE 67 NORTH AMERICA: MARKET SNAPSHOT
- FIGURE 68 ASIA PACIFIC: MARKET SNAPSHOT
- FIGURE 69 BUSINESS SEGMENT REVENUE ANALYSIS, 2020–2022 (USD BILLION)
- FIGURE 70 MARKET SHARE ANALYSIS FOR KEY COMPANIES, 2022
- FIGURE 71 COMPANY EVALUATION MATRIX (KEY PLAYERS), 2022
- FIGURE 72 COMPANY EVALUATION MATRIX (STARTUPS/SMES), 2022
- FIGURE 73 FINANCIAL METRICS OF KEY SECURITY AUTOMATION VENDORS
- FIGURE 74 YTD PRICE TOTAL RETURN AND STOCK BETA OF KEY SECURITY AUTOMATION VENDORS
- FIGURE 75 PALO ALTO NETWORKS: COMPANY SNAPSHOT
- FIGURE 76 SPLUNK: COMPANY SNAPSHOT
- FIGURE 77 CYBERARK: COMPANY SNAPSHOT
- FIGURE 78 CHECK POINT: COMPANY SNAPSHOT
- FIGURE 79 CROWDSTRIKE: COMPANY SNAPSHOT
- FIGURE 80 CISCO: COMPANY SNAPSHOT
- FIGURE 81 IBM: COMPANY SNAPSHOT
- FIGURE 82 SECUREWORKS: COMPANY SNAPSHOT
- FIGURE 83 TENABLE: COMPANY SNAPSHOT
The security automation market research study involved extensive secondary sources, directories, journals, and paid databases. Primary sources were mainly industry experts from the core and related industries, preferred security automation providers, third-party service providers, consulting service providers, end users, and other commercial enterprises. In-depth interviews were conducted with various primary respondents, including key industry participants and subject matter experts, to obtain and verify critical qualitative and quantitative information, and assess the market’s prospects.
Secondary Research
In the secondary research process, various sources were referred to, for identifying and collecting information for this study. Secondary sources included annual reports, press releases, and investor presentations of companies; white papers, journals, and certified publications; and articles from recognized authors, directories, and databases. The data was also collected from other secondary sources, such as journals, government websites, blogs, and vendors websites. Additionally, security automation spending of various countries was extracted from the respective sources. Secondary research was mainly used to obtain key information related to the industry’s value chain and supply chain to identify key players based on solutions, services, market classification, and segmentation according to offerings of major players, industry trends related to solutions, services, deployment modes, mode of channel, business functions, conversational interfaces, verticals, and regions, and key developments from both market- and technology-oriented perspectives.
Primary Research
In the primary research process, various primary sources from both supply and demand sides were interviewed to obtain qualitative and quantitative information on the market. The primary sources from the supply side included various industry experts, including Chief Experience Officers (CXOs); Vice Presidents (VPs); directors from business development, marketing, and security automation expertise; related key executives from security automation solution vendors, SIs, professional service providers, and industry associations; and key opinion leaders.
Primary interviews were conducted to gather insights, such as market statistics, revenue data collected from solutions and services, market breakups, market size estimations, market forecasts, and data triangulation. Primary research also helped understand various trends related to technologies, applications, deployments, and regions. Stakeholders from the demand side, such as Chief Information Officers (CIOs), Chief Technology Officers (CTOs), Chief Strategy Officers (CSOs), and end users using security automation solutions, were interviewed to understand the buyer’s perspective on suppliers, products, service providers, and their current usage of security automation solutions and services, which would impact the overall security automation market.
The breakup of Primary Research
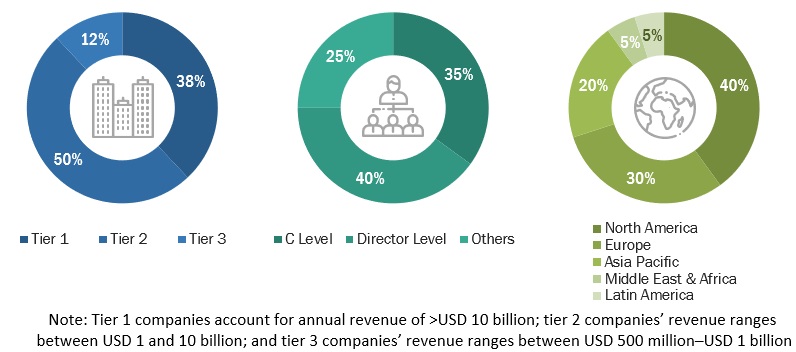
To know about the assumptions considered for the study, download the pdf brochure
|
COMPANY NAME |
DESIGNATION |
|
Torq |
Director of Product |
|
Secureworks |
Security Consultant |
|
Devo Technology |
Senior Software Engineer |
Market Size Estimation
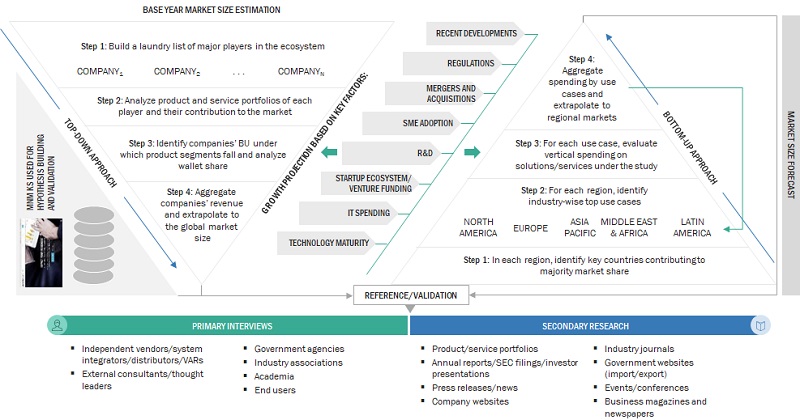
In the bottom-up approach, the adoption rate of security automation solutions and services among different end users in key countries concerning their regions contributing the most to the market share was identified. For cross-validation, the adoption of security automation solutions and services among industries and different use cases concerning their regions was identified and extrapolated. Weightage was given to use cases identified in different regions for the market size calculation.
Based on the market numbers, the regional split was determined by primary and secondary sources. The procedure included the analysis of the security automation market’s regional penetration. Based on secondary research, the regional spending on Information and Communications Technology (ICT), socio-economic analysis of each country, strategic vendor analysis of major security automation providers, and organic and inorganic business development activities of regional and global players were estimated. With the data triangulation procedure and data validation through primaries, the exact values of the overall security automation market size and segments’ size were determined and confirmed using the study.
Global Security Automation Market Size: Bottom-Up and Top-Down Approach:
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
Based on the market numbers, the regional split was determined by primary and secondary sources. The procedure included the analysis of the security automation market’s regional penetration. Based on secondary research, the regional spending on Information and Communications Technology (ICT), socio-economic analysis of each country, strategic vendor analysis of major security automation providers, and organic and inorganic business development activities of regional and global players were estimated. With the data triangulation procedure and data validation through primaries, the exact values of the overall security automation market size and segments’ size were determined and confirmed using the study.
Market Definition
Security automation is the use of technology that performs tasks with reduced human assistance to integrate security processes, applications, and infrastructure. Security automation solutions for IT systems can allow the IT teams more time to focus on complex projects instead of routine, repetitive tasks such as provisioning and scripting.
Stakeholder
- Security automation vendors
- Security automation service vendors
- Managed service providers
- Support and maintenance service providers
- System Integrators (SIs)/migration service providers
- Value-Added Resellers (VARs) and distributors
- Distributors and Value-added Resellers (VARs)
- System Integrators (SIs)
- Independent Software Vendors (ISV)
- Third-party providers
- Technology providers
Report Objectives
- To define, describe, and predict the security automation market by offering (solutions and services), code type, technology, application, verticals, and region
- To provide detailed information related to major factors (drivers, restraints, opportunities, and industry-specific challenges) influencing the market growth
- To analyze the micro markets with respect to individual growth trends, prospects, and their contribution to the total market
- To analyze the opportunities in the market for stakeholders by identifying the high-growth segments of the security automation market
- To analyze opportunities in the market and provide details of the competitive landscape for stakeholders and market leaders
- To forecast the market size of segments for five main regions: North America, Europe, Asia Pacific, Middle East & Africa, and Latin America
- To profile key players and comprehensively analyze their market rankings and core competencies
- To analyze competitive developments, such as partnerships, new product launches, and mergers and acquisitions, in the security automation market
- To analyze the impact of recession across all the regions across the security automation market
Available Customizations
With the given market data, MarketsandMarkets offers customizations as per your company’s specific needs. The following customization options are available for the report:
Product Analysis
- Product quadrant, which gives a detailed comparison of the product portfolio of each company.
Geographic Analysis
- Further breakup of the North American security automation market
- Further breakup of the European security automation market
- Further breakup of the Asia Pacific security automation market
- Further breakup of the Middle Eastern & African security automation market
- Further breakup of the Latin America security automation market
Company Information
- Detailed analysis and profiling of additional market players (up to five)













Growth opportunities and latent adjacency in Security Automation Market