Content Security Market by Component (Solutions, Services), by Solutions (E-Mail Content Security, Web Content Security, Others), by Organization Size, by Vertical (BFSI, IT and ITeS, Retail and eCommerce, Media and Entertainment) and by Region - Global Forecast to 2027
The Content Security Policy improve the document’s security. It can limit how resources like JavaScript, CSS, HTML frames, and web workers are used that loads the browser. It is mostly used as a header for a HTTP response. CSP gives website owners a standard way to declare content origins that have been approved and should be allowed to be loaded by browsers on that website.
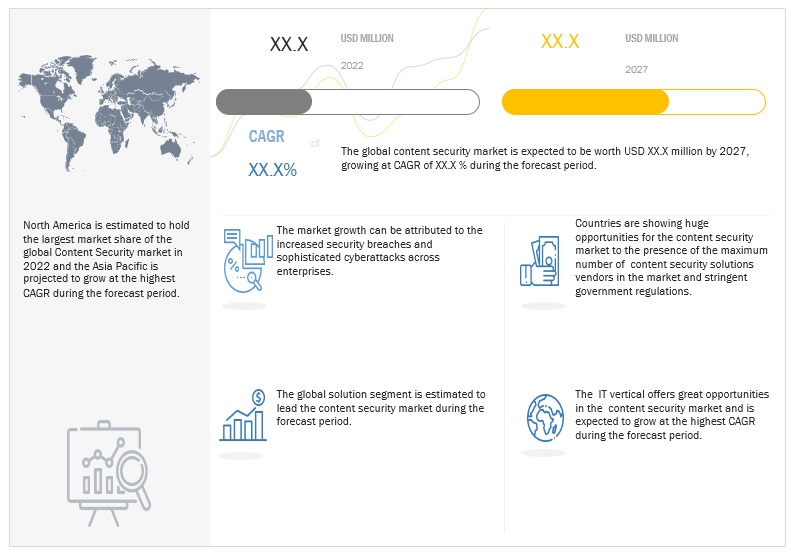
The global content security market size is estimated to grow from USD XX million in 2022 to USD XX million by 2027, at a CAGR of XX%. The purpose of the security standard widely adopted practice was to stop code injection attacks like clickjacking, cross-site scripting (XSS), and others that occur when malicious content is run in the trusted web page context.
To know about the assumptions considered for the study, Request for Free Sample Report
Driver: Web Security.
In the era of startups and subsequent website launches for the general public, the potential security risks that could affect the nature of the business or the privacy of end users were brought to light and emphasized. For instance, according to Siteefy, there are approximately 175 brand-new websites built each minute. Thus, approximately 252,000 brand-new websites are created each day worldwide.
Increased digitalization and adoption of IoT.
Due to the need for real-time threat protection, increased IT spending and investments, and rising demand for cloud-based applications, the global content security market is anticipated to expand at an exponential rate.
Challenge: Lack of supervising laws and regulations
The adoption of content security solutions is hampered by the integration of content security tools for various industry sectors and clients, posing a challenge to the market's expansion. For instance, there are loose security policies in place, lack of watermarking, minimal permissions/ open access, lack of encryption, work home routers, no network control, and third-party vendors outside the system. All these factors are acting as a barrier to content security’s global expansion.
Key Market Players
Cartesian Inc. (US), Microsoft Corporation (US), Trend Micro Inc. (Japan), Check point Software Technologies (Israel), Barracuda Networks (US), Sophos Technologies Pvt. Ltd (UK)., Proofpoint (US), Forcepoint (US), Verimetrix (France), Lookout (US), CommScope (US) and Infosec Information Technologies (Istanbul) are few key players in the content security market.
Recent developments:
- In 2022, the world's leading initiative for film and television content security, The Trusted Partner Network (TPN), is expanding its program to better serve the media and entertainment industry as it continues to grow globally and in complexity and now conducts much of its business in the cloud.
- In China 2021, research had been done on the growth of artificial intelligence and how it affected content security. (Content security based on AI)

TABLE OF CONTENTS
1 INTRODUCTION
1.1 STUDY OBJECTIVES
1.2 MARKET DEFINITION
1.2.1 INCLUSIONS AND EXCLUSIONS
1.3 MARKET SCOPE
1.3.1 MARKET COVERED
1.3.2 GEOGRAPHIC SCOPE
1.3.3 YEARS CONSIDERED FOR THE STUDY
1.4 CURRENCY CONSIDERED
1.5 STAKEHOLDERS
1.6 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY
2.1 RESEARCH DATA
2.1.1 SECONDARY DATA
2.1.2 PRIMARY DATA
2.1.2.1 Breakup of primaries
2.1.2.2 Key industry insights
2.2 MARKET BREAKUP AND DATA TRIANGULATION
2.3 MARKET SIZE ESTIMATION
2.4 MARKET FORECAST
2.5 RESEARCH ASSUMPTIONS
2.6 LIMITATIONS OF THE STUDY
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
5 MARKET OVERVIEW AND INDUSTRY TRENDS
5.1 INTRODUCTION
5.2 MARKET DYNAMICS
5.2.1 DRIVERS
5.2.2 RESTRAINTS
5.2.3 OPPORTUNITIES
5.2.4 CHALLENGES
5.3 USE CASES
5.4 VALUE CHAIN ANALYSIS
5.5 ECOSYSTEM
5.6 PORTER’S FIVE FORCES MODEL ANALYSIS
5.7 AVERAGE SELLING PRICE ANALYSIS
5.8 TECHNOLOGY ANALYSIS
5.9 PATENT ANALYSIS
5.10 TRENDS/DISRUPTIONS IMPACTING THE CUSTOMER’S BUSINESS
5.11 TARIFF AND REGULATORY LANDSCAPE
5.11.1 REGULATORY BODIES, GOVERNMENT AGENCIES AND OTHER ORGANIZATIONS
5.12 KEY STAKEHOLDERS AND BUYING CRITERIA
5.12.1 KEY STAKEHOLDERS IN BUYING PROCESS
5.13 KEY CONFERENCES AND EVENTS IN 2022-23
6 CONTENT SECURITY MARKET, BY OFFERING
6.1 INTRODUCTION
6.2 SOLUTION
6.2.1 E-MAIL CONTENT SECURITY
6.2.2 WEB CONTENT SECURITY
6.2.2 OTHERS
6.3 SERVICES
7 CONTENT SECURITY MARKET, BY ORGANIZATION SIZE
7.1 INTRODUCTION
7.2 SMALL AND MEDIUM-SIZED ENTERPRISES (SMES)
7.3 LARGE ENTERPRISES
8 CONTENT SECURITY MARKET, BY VERTICAL
8.1 INTRODUCTION
8.2 BANKING, FINANCIAL SERVICES, AND INSURANCE (BFSI)
8.3 IT AND ITES
8.4 MEDIA AND ENTERTAINMENT
8.5 MANUFACTURING
8.6 HEALTHCARE
8.7 RETAIL AND ECOMMERCE
8.8 OTHER VERTICALS
9 CONTENT SECURITY MARKET, BY REGION
9.1 INTRODUCTION
9.2 NORTH AMERICA
9.3 EUROPE
9.4 ASIA PACIFIC (APAC)
9.5 MIDDLE EAST AND AFRICA (MEA)
9.6 LATIN AMERICA
10 COMPETITIVE LANDSCAPE
10.1 OVERVIEW
10.2 MARKET EVALUATION FRAMEWORK
10.3 REVENUE ANALYSIS OF LEADING PLAYERS
10.4 MARKET SHARE ANALYSIS OF THE TOP MARKET PLAYERS
10.5 HISTORICAL REVENUE ANALYSIS
10.6 RANKING OF KEY PLAYERS IN THE CONTENT SECURITY MARKET
10.7 KEY COMPANY EVALUATION QUADRANT
10.7.1 STARS
10.7.2 EMERGING LEADERS
10.7.3 PERVASIVE PLAYERS
10.7.4 PARTICIPANTS
10.8 COMPETITIVE BENCHMARKING
10.8.1 KEY COMPANY EVALUATION CRITERIA
10.8.2 SME/STARTUP COMPANY EVALUATION CRITERIA
10.9 SME/STARTUP EVALUATION QUADRANT
10.9.1 PROGRESSIVE COMPANIES
10.9.2 RESPONSIVE COMPANIES
10.9.3 DYNAMIC COMPANIES
10.9.4 STARTING BLOCKS
10.10 COMPETITIVE SCENARIO AND TRENDS
10.10.1 NEW PRODUCT LAUNCHES AND PRODUCT ENHANCEMENTS
10.10.2 DEALS
11 COMPANY PROFILES
*Note – details on business overview, company financial snapshot (public listed companies only), solutions and services offered, recent developments, and other key insights will be covered.
Also, based on the market segmentations a list of vendors will be shortlisted tentatively for the profiling section and finalized based on further assessment.
11.1 KEY PLAYERS*
11.1.1 CARTESIAN INC
11.1.2 MICROSOFT
11.1.3 VERIMETRIX
11.1.4 LOOKOUT
11.1.5 TREND MICRO INC
11.1.6 FORCEPOINT
11.1.7 CHECK POINT SOFTWARE TECHNOLOGIES
11.1.8 BARRACUDA NETWORKS
11.1.9 SYNOPSYS
11.1.10 PROOFPOINT
11.1.11 COMMSCOPE
11.1.12 INFOSEC INFORMATION TECHNOLOGIES
11.1.13 OTHERS
11.2 OTHER PLAYERS
12 ADJACENT MARKETS
12.1 INTRODUCTION TO ADJACENT MARKETS
12.2 LIMITATIONS
12.3 CONTENT SECURITY : ADJACENT MARKETS
12.4 ADJACENT MARKET 1
12.5 ADJACENT MARKET 2
13 APPENDIX
13.1 DISCUSSION GUIDE
13.2 KNOWLEDGE STORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
13.3 AVAILABLE CUSTOMIZATIONS
13.4 RELATED REPORTS
13.5 AUTHOR DETAILS
[Note -This is a tentative table of content. The scope of the study is subject to be modified/changed during the course of the study]













Growth opportunities and latent adjacency in Content Security Market